Applies To:
Show Versions
BIG-IQ Centralized Management
- 6.1.0
Monitoring Ongoing DDoS Attacks
Detecting the impact of DDoS attacks on protected objects
-
Adjust the protection mode of your DoS profile (mitigating as opposed to monitoring)
-
Edit or reassign a DoS profile
-
Configure additional resources for your BIG-IP devices to maintain their protection services
Isolate ongoing DDoS attacks
- A BIG-IQ data collection device configured for the BIG-IQ device
- The BIG-IP device located in your network and running a compatible software version
- Statistics collection enabled for managed BIG-IP devices
Protection modes against DDoS attacks
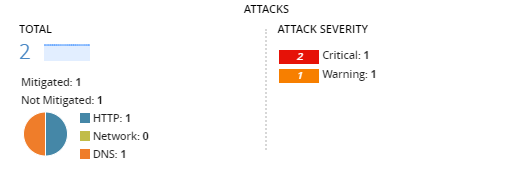
The attack protection mode indicates whether your DoS profile's configuration mitigates or monitors detected attacks based on the security services provisioned on your BIG-IP devices (ASM, DNS, and AFM).
Mitigated
The DoS profile that reported the attack has at least one mitigating element:
- HTTP protocol (Application Security): One or more operation modes is configured to Blocking.
- DNS protocol or Network protocol: One or more attack type states is configured to Mitigate.
Not Mitigated
The DoS profile that reported the attack has at least one monitoring element, and no mitigating elements:
- HTTP protocol (Application Security): One or more operation modes is configured to Transparent.
- DNS protocol or Network protocol: One or more attack type states is configured to Detect Only or Learn Only.
DDoS attack severity
The severity assigned to the DDoS attacks displayed in the Protection Summary screen () have either a Critical (2) or Warning (1) attack score. The score reflects the recently reported correlated attack with the highest attack severity. Severity is based on the following criteria.
Detection Mode
The attack's detection mode (trigger) influences the weight of the attack severity.
IP Ratio
The ratio of different attacking client IP addresses, out of all client IP addresses processed. An increased number of IP addresses attacking indicates a broader attack distribution.
Mitigated traffic
The ratio of mitigated traffic out of all traffic processed.
Identifying ongoing HTTP DDoS attacks
A DoS profile can actively mitigate or monitor an HTTP DDoS attack according to your profile's configuration. Once you have isolated a recently detected, or ongoing, HTTP attack, you can further isolate details of the attack. You can view additional details about a specific attack, or set of correlated attacks, to ensure that your current DoS profile configuration meets your Application Security requirements.
- BIG-IQ data collection device configured for the BIG-IQ device.
- The BIG-IP device is located in your network and running the compatible software versions of 13.1.1.4, 14.0.0.3, or 14.1.
- BIG-IP Web Application Security (ASM) services is discovered on BIG-IQ.
- Statistics collection enabled for managed BIG-IP devices.
- A DoS profile with Application Security enabled.
Identify DDoS attacks that can impact application security
Modifying a DoS profile to improve application protection
A DoS profile configured on the BIG-IQ Centralized Management system prevents or monitors denial of service (DoS) attacks on web applications. Depending on your configuration, the system detects DoS attacks based on transactions per second (TPS) on the client side, stress-based server latency, heavy URLs, source location, suspicious browsers, and failed CAPTCHA responses. Behavioral DoS (BADoS), a part of stress-based detection, automatically discovers and mitigates DoS attacks using behavioral data.
Changes in your application's traffic might reduce the effectiveness of your existing DoS profile. You can edit DoS profiles that protect your application's security to add or remove attack detection and mitigation measures.
Edit DoS profile for application security
Identifying ongoing network DDoS attacks
A DoS Profile can actively mitigate or monitor network DDoS attacks according to your profile's configuration. Once you have isolated recently detected, or ongoing network protocol attack, you can further isolate details of the attack. You can the view additional details about an ongoing attack detected by your BIG-IP environment, to ensure that your current DoS profile configuration meets your Network Security requirements.
The Protection Summary screen () gives details of DDoS attacks for the network protocol. To display attack information on this screen, your configuration must have the following characteristics:
- BIG-IQ data collection device configured for the BIG-IQ device.
- BIG-IP device located in your network and running a compatible software version of 13.1.1.4 or later.
- BIG-IP Network Security (AFM) services discovered on BIG-IQ.
- Statistics collection enabled for managed BIG-IP devices.
- A DoS profile with Network Security enabled.
Identify DDoS attacks that can impact network security
Modifying a DoS profile to improve Network Security
A DoS profile configured on BIG-IQ Centralized Management prevents or monitors DoS attacks on your application. Changes in your traffic or new attack types might reduce a DoS profile's capability to protect your network. You can edit DoS profiles attached to the virtual servers that provide Network Security services.
Edit DoS profile for Network Security
Identifying ongoing DNS DDoS attacks
A DoS profile can actively mitigate or monitor DNS DDoS attacks according to your profile's configuration. Once you have isolated a recently detected, or ongoing, DNS DDoS attack, you can further isolate details of the attack. You can view additional details about a specific attack, or set of correlated attacks, to ensure that your current DoS profile configuration meets your DNS Security requirements.
- BIG-IQ data collection device configured for the BIG-IQ device.
- BIG-IP device located in your network and running a compatible software version 13.1.1.4 or later.
- BIG-IP DNS services discovered on BIG-IQ.
- Statistics collection enabled for managed BIG-IP devices.
- A DoS profile with DNS Security enabled.
Identify DDoS attacks that can impact DNS security
Modifying a DoS profile to improve DNS security
A DoS profile configured on BIG-IQ Centralized Management prevents or monitors DoS attacks on your application. Changes in your traffic or a new attack type (query) might reduce a DoS profile's capability to protect your DNS servers. You can edit DoS profiles attached to the virtual servers that provide DNS security.
Edit DoS profile for DNS security
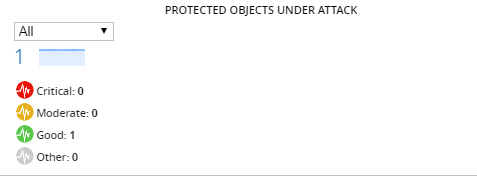
Isolate status of protected objects under attack
- A BIG-IQ data collection device configured for the BIG-IQ device
- The BIG-IP device located in your network and running a compatible software version
- Statistics collection enabled for managed BIG-IP devices
Rules for correlated DoS attacks
Attacks detected from multiple BIG-IP devices may be correlated with an ongoing attack if they meet the following criteria, per security protocol. You can view correlated attack alerts either in the Attack Details screen () or Alert History screen ().
HTTP
- DoS Profile name
- Device Service Cluster (DSC) name
- Application
DNS
- DoS Profile name
- Virtual server name or Device Sync Group
- Device Service Cluster (DSC) name
Network
Reported DNS attacks correlate if they share the following characteristics:
- DoS Profile name
- Virtual server nameNote: A network attack on a device level correlates attacks with the virtual server name Device.
- Device Service Cluster (DSC) name
DDoS attack events
The BIG-IP system defines an attack by assigning an attack ID. The shared characteristics within the DDoS attack's data can correlate different attack IDs across a BIG-IP system environment (see Rules for correlated DoS attacks). These correlated attacks trigger events that allow you to evaluate a single attack's overall status, severity, and system impact. Attack inactivity indicates the end of a DDoS attack, which triggers a cleared event.
Raw attack events
Raw attack events report on the basis of a single attack ID reported by the BIG-IP system. Any changes in a raw attack's dimensions or severity are reflected in the raw attack events.
Correlated attack events
Correlated attack events report on the basis of the raw attack events that comprise a single correlated attack. Correlated events occur as a result of significant modifications to an attack's state across your BIG-IP system environment.
-
A change in the highest reported status out of the active raw attacks that comprise the correlated attack:
-
Attack severity
-
Attack mitigation (this also impacts the corresponding attack trigger).
-
-
The correlated attack was detected by an additional BIG-IP blade or hostname.
-
The addition or removal of a raw attack.
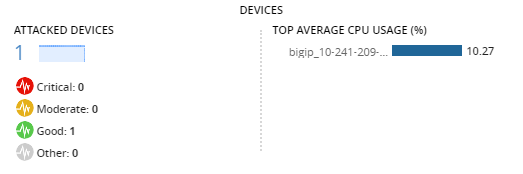
Detecting health issues in BIG-IP devices reporting DDoS attacks
BIG-IP services secure your protected objects from DDoS attacks, based on your security configuration and your DoS profile. It is important to ensure that the BIG-IP devices hosting these protection services have enough resources to withstand these attacks.
BIG-IP devices, or service scaling groups (SSG), receive a health score based on a configurable resource usage threshold (CPU, memory, throughput etc.). You can identify devices with low health that provide security services, to mitigate or monitor these resources to prevent issues with your system's performance.
Identify devices with low health managing DDoS attacks
Device health alerts
The device health alert notifies you of changes in device resource and throughput metric thresholds for your BIG-IP devices. To view your device health thresholds, go to the Alert Rules screen and select the default device rules (.
| Alert | Description | Indication | Default Thresholds | Action (if applicable) |
|---|---|---|---|---|
| Device Health | There has been a change in one or more of the of BIG-IP device health rule metrics. | One or more of the device resources and/or throughput measurements crossed a defined threshold, which may impact your BIG-IP device's performance. | For SSG devices: Customized rules per service scaling group. | For SSG devices: A critical health status of your BIG-IP
device might trigger a scale-out event. Investigate the active alerts for device
metrics. For stand-alone BIG-IP devices: Investigate BIG-IP devices with critical or moderate health to adjust or add resources. |