Applies To:
Show Versions
F5 DDoS Hybrid Defender
- 14.1.0
Introducing DDoS Hybrid Defender
Introduction to DDoS Hybrid Defender
F5® DDoS Hybrid Defender™ protects your organization against a wide range of DDoS attacks using a multi-pronged approach. By combining on-premises and cloud technologies, analytics, and advanced methods, DDoS Hybrid Defender is a hybrid solution that detects network and application layer attacks, and is easy to deploy and manage.
DDoS Hybrid Defender mitigates against the full spectrum of DDoS attacks including:
- Network capacity attacks
- DNS and SIP protocol volumetric attacks
- HTTP and HTTPS volumetric attacks
- HTTP and HTTPS CPU-based (heavy URL) attacks
You can specify which objects to protect on the network, assigning the appropriate protections to network devices and application servers, and prevent attackers from exhausting network resources and impacting application availability. DDoS Hybrid Defender can be installed for high availability (two systems) or as a stand-alone system.
DDoS deployments
The deployment you use for DDoS Hybrid Defender™ depends on the needs of your organization. For maximum DDoS protection, it is recommended that you deploy DDoS Hybrid Defender inline. However, it can also be deployed out of band, or in locations where symmetric data flows are not guaranteed. Typical locations for the placement of DDoS Hybrid Defender are at the edge of the network or at the edge of the data center as shown in the figure.
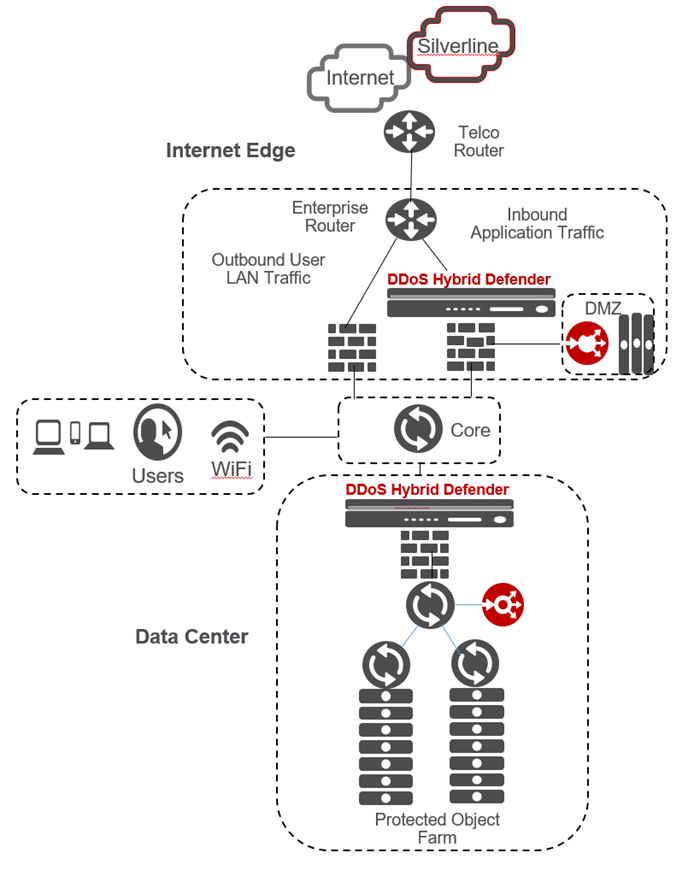
Points in the network for DDoS defense
Inline deployment
DDoS Hybrid Defender provides maximum protection when deployed inline in one of two ways:
- Bridged mode with VLAN groups
- Routed mode
For bridged mode, you can place DDoS Hybrid Defender in transparent mode on a link between two Layer 3 devices. This way, the IP addresses on each end of the link do not have to change. You do this by creating VLAN groups on DDoS Hybrid Defender. The VLANs and the VLAN group configured are purely internal, and are used to bridge traffic from one port to another within DDoS Hybrid Defender.
For routed mode, you can insert DDoS Hybrid Defender at the edge of the network without disturbing the current configuration. It is possible to pick and choose the networks whose traffic goes through the DDoS Hybrid Defender, and let the rest continue to follow the path it was previously taking.
Step by step instructions are provided in the installation chapter.
Out of band deployment
You can deploy DDoS Hybrid Defender out of band in two ways:
- Set up a Layer 2 switch with span ports so that it mirrors traffic onto DDoS Hybrid Defender.
- Configure network devices so that they send Netflow data to DDoS Hybrid Defender.
If using span ports, you can configure DDoS Hybrid Defender to perform DDoS detection by listening to traffic that is mirrored from a Layer 2 switch. Of the various ports that can be mirrored on the DDoS Hybrid Defender, it is usually best to mirror the Layer 2 switch ports that connect to the firewall. Since firewalls are stateful devices, traffic typically flows through them in a symmetric fashion. Thus, mirroring the ports connected to the firewalls is a good way to send all the packets in a session directed through the firewall and on to DDoS Hybrid Defender. Using span ports, DDoS Hybrid Defender can use all L2 to L7 DDoS detection mechanisms.
Alternatively, you can configure DDoS Hybrid Defender to detect DDoS attacks by examining Netflow traffic sent to it. In this case, you can deploy DDoS Hybrid Defender anywhere in the network and configure it to receive Netflow streams on a Netflow listener IP address and port. Netflow traffic should be allowed through any firewalls that are in the path from devices sending Netflow data to the DDoS Hybrid Defender.
Step by step instructions are provided in the installation chapter.
Example DDoS Hybrid Defender deployment
DDoS Hybrid Defender™ guards against multiple types of attacks including protection for the device, protection for the data center, networks, and, optionally, offloading using F5 Silverline® cloud-based services.
Here is how it works: A DDoS Hybrid Defender™ system that is deployed in your network defends against DDoS Layer 3 through Layer 7 attacks as long the upstream Internet pipe is not saturated. When the upstream pipe is flooded, DDoS Hybrid Defender can signal the F5 Silverline Cloud Platform to help mitigate the attack. DDoS Hybrid Defender sends Silverline Cloud Platform the information that an attack was detected, and provides the application or CIDR definition, destination subnet, attack type, and the attack size.
The Hybrid Signaling feature enables enterprises with DDoS Hybrid Defender to integrate with F5 Silverline to divert traffic during large attacks. The F5 Silverline Cloud Platform scrubs the volumetric attack traffic and forwards the clean traffic to the customer’s networks. The clean traffic is sent through GRE tunnels that were set up between the Silverline scrubbing centers and the customer’s networks.
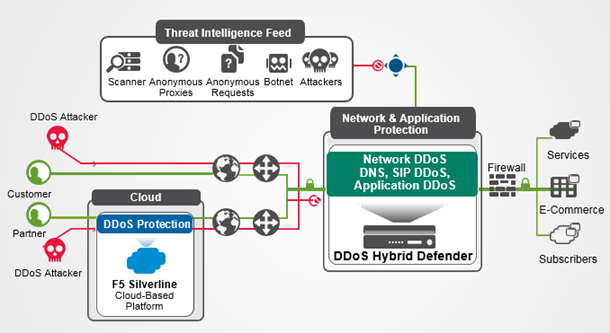
Example DDoS Hybrid Defender deployment





