Applies To:
Show Versions
F5 DDoS Hybrid Defender
- 14.0.0
Installing DDoS Hybrid Defender for High Availability
Overview: Installing DDoS Hybrid Defender for High Availability
You can install DDoS Hybrid Defender™ onto a dedicated system (device 1) and set up a failover system that automatically takes over in case of system failure (device 2). The system processing traffic is called the active system. A second system is set up as a standby system, and data is synchronized between the active and standby systems. If the active system goes offline, the standby system becomes active, and begins processing traffic and protecting against DDoS attacks.
You can assign the management IP addresses from the LCD panel of the devices, or with a hypervisor if you are using the Virtual Edition.
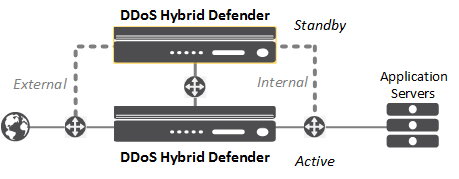
DDoS Hybrid Defender High-Availability deployment
You must have two DDoS Hybrid Defender systems to set up high availability. Before you begin, make sure you have this information for both devices:
- Base registration key
- Management IP address, network mask, and management route IP address
- Passwords for the root and admin accounts
- NTP server IP address (optional)
- Remote DNS lookup server IP address (required for F5 Silverline® integration or if resolving host names)
Performing initial setup
Manually licensing DDoS Hybrid Defender
Connecting two DDoS Hybrid Defender devices
When installing two systems for high availability, the system you plan to set up as the active system, device 1, must be the system with the highest management IP address.
- Connect the two DDoS Hybrid Defender™ devices as required by your network configuration.
- Note the interfaces and VLAN used to connect the devices.
Connecting with F5 Silverline
DDoS Hybrid Defender is now integrated with the Silverline Cloud Platform.
Configuring high availability on device 1
Checking the status of DDoS Hybrid Defender on device 2
Configuring the network for high availability
Configuring the network using routed mode
Deploying inline using virtual wire
Deploying inline using VLAN groups
Examining traffic metadata using Netflow messages
Setting up remote logging
When configuring remote high-speed logging of system events, it is helpful to understand the objects you need to create and why, as described here:
| What to create | Why |
|---|---|
| Pool | Create a pool of remote log servers to which the BIG-IP system can send log messages. |
| Destination | Create a log destination of Remote High-Speed Log type that specifies a pool of remote log servers. If your remote log servers are the ArcSight, Splunk, IPFIX, or Remote Syslog type, create an additional log destination to format the logs in the required format and forward the logs to a remote high-speed log destination. |
| Publisher | Create a log publisher to send logs to a set of specified log destinations. |
| Logging profile | Create a logging profile to enable logging of user-specified data at a user-specified level, and associate a log publisher with the profile. |
| Protected object | Associate a logging profile with a protected object to define how the system logs security events on the traffic that the protected object processes. |
Following are the general steps to set up remote logging:
- Create a pool of remote servers to which the system can send log messages: on the Main tab, click , create, then add the log servers and ports.
- Create a remote high-speed log destination: on the Main tab, click , create, specify the type, and any other settings for the remote log destination.
- Create a publisher for the system to send log messages: on the Main tab, click , create, and select the log destinations for the publisher.
-
Create a logging profile: on the Main tab, click , create, select the types of logs, and complete the associated
settings.
- Network Firewall provides logs for IP intelligence and traffic statistics.
- DoS Protection provides logs for DNS, SIP, and Network DoS events.
- Bot Defense provides logs for HTTP DoS protection for application security.
- Associate the logging profile with the appropriate protected object: on the Main tab, click , click the name of the protected object. In the properties pane on the right, select the logging profile to use.
Event logs from DDoS Hybrid Defender are sent to the remote logging server in the format you specified.





