Applies To:
Show Versions
BIG-IP LTM
- 11.5.10, 11.5.9, 11.5.8, 11.5.7, 11.5.6, 11.5.5, 11.5.4, 11.5.3, 11.5.2, 11.5.1
Using NAT44 to Translate IPv4 Addresses
About NAT44
For the BIG-IP® system CGNAT module, NAT44 is the NAT type that maps IPv4 subscriber private addresses to IPv4 Internet public addresses. Translation addresses and ports are set in LSN pools. The CGNAT module performs NAT44 translations for all IP traffic.
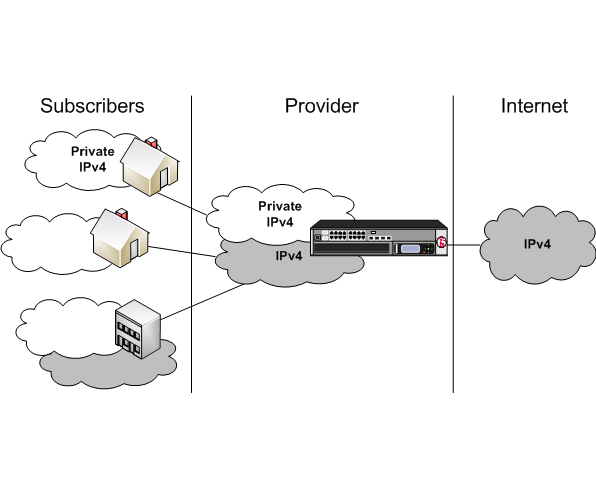
Diagram of a NAT44 network
About CGNAT hairpinning
An optional feature on the BIG-IP ®system, hairpinning routes traffic from one subscriber's client to an external address of another subscriber's server, where both client and server are located in the same subnet. To each subscriber, it appears that the other subscriber's address is on an external host and on a different subnet. The BIG-IP system can recognize this situation and send, or hairpin, the message back to the origin subnet so that the message can reach its destination.





