Applies To:
Show Versions
BIG-IP AAM
- 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP Analytics
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP Link Controller
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP LTM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP AFM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP PEM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP DNS
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP ASM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
Implementing External Cryptographic Server Offload with BIG-IP Systems
Overview: Implementing external cryptographic server offload
You can offload cryptographic operations to an external BIG-IP® system. For example, you can set up an LTM VE instance (the crypto client) to offload cryptographic operations, such as an RSA decryption operation for an SSL handshake, to an external BIG-IP system (the crypto server) that supports crypographic hardware acceleration.
In general, the setup process includes configuring a client BIG-IP system as a crypto client and a server BIG-IP system as a crypto server, and ensures secure communication between the end user, the crypto client, and the crypto server.
This illustration depicts an external cryptographic offload configuration.
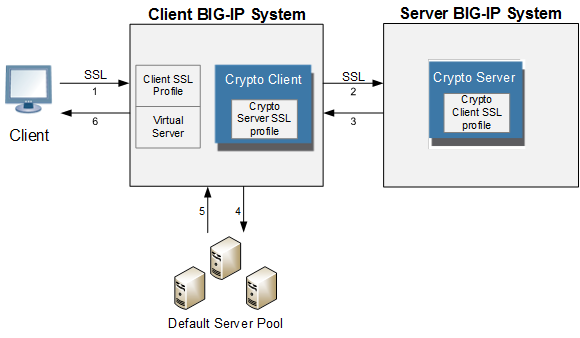
The illustration shows the BIG-IP configuration objects that are required for implementing the external cryptographic server offload feature, as well as the flow of client traffic that occurs. In the illustration, one BIG-IP system includes a virtual server configured with the destination IP address for application traffic coming from a client system. Because the client traffic uses SSL, the BIG-IP system with the virtual server must include a standard Client SSL profile, which causes cryptographic functions to be offloaded from the selected destination server (pool member) to that BIG-IP system.
Once this BIG-IP system has assumed cryptographic functions from the destination server, the BIG-IP system can offload these functions to another BIG-IP system to handle the actual cryptographic processing. To enable the BIG-IP system to offload the cryptographic processing to another BIG-IP system, you must designate the two BIG-IP systems as a crypto client and crypto server, and you must create an SSL profile on each system that is optimized for BIG-IP-to-BIG-IP cryptographic processing (a crypto-optimized Server SSL profile for the BIG-IP crypto client and crypto-optimized Client SSL profile for the BIG-IP crypto server).
Task summary
Creating a Client SSL profile on a client BIG-IP system
You create a Client SSL profile on a client BIG-IP® system to authenticate and decrypt/encrypt client-side application traffic.
Creating a pool on a client BIG-IP system
Creating a virtual server on a client BIG-IP system
Creating a Server SSL profile on a client BIG-IP system
Creating a crypto client object on a client BIG-IP system
Creating a Client SSL profile on a server BIG-IP system
You create a Client SSL profile on a server BIG-IP® system to authenticate and decrypt/encrypt application traffic from the client BIG-IP system.





