Applies To:
Show Versions
BIG-IP AAM
- 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP Analytics
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP Link Controller
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP LTM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP AFM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP PEM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP DNS
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
BIG-IP ASM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1
Securing Client-Side and Server-Side LDAP Traffic
Overview: Securing LDAP traffic with STARTTLS encryption
You can configure STARTTLS encryption for Lightweight Directory Access Protocol (LDAP) traffic passing through the BIG-IP® system. LDAP is an industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network.
You configure the BIG-IP system for STARTTLS encryption by configuring Client LDAP and Server LDAP profiles to activate the STARTTLS communication protocol for any client or server traffic that allows or requires STARTTLS encryption.
Normally, LDAP traffic between LDAP servers and clients is unencrypted. This creates a privacy issue because LDAP traffic often passes through routers that the servers and clients do not trust, resulting in a third party potentially changing the communications between the server and client. Also, two LDAP systems do not normally authenticate each other. A more secure LDAP server might only allow communications from other known LDAP systems, or the server might act differently with unknown systems.
To mitigate these problems, the BIG-IP system includes two LDAP profiles that you can configure. When you configure a Client LDAP or Server LDAP profile, you can instruct the BIG-IP system to activate the STARTTLS communication protocol for any client or server traffic that allows or requires STARTTLS encryption. The STARTTLS protocol effectively upgrades a plain-text connection to an encrypted connection on the same port (port 389), instead of using a separate port for encrypted communication.
This illustration shows a basic configuration of a BIG-IP system that activates STARTTLS to secure LDAP traffic between a client system and the BIG-IP system, and between the BIG-IP system and an LDAP authentication server.
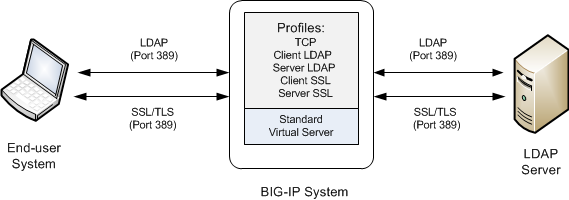
Sample BIG-IP configuration for LDAP traffic with STARTTLS activation
Task summary
To configure the BIG-IP ®system to process Lightweight Directory Access Protocol (LDAP) traffic with TLS encryption, you perform a few basic tasks.
Task list
Creating a Client LDAP profile
You perform this task to specify the condition under which the BIG-IP system should activate STARTTLS encryption for client-side traffic destined for a specific virtual server.
Creating a Server LDAP profile
You perform this task to specify the condition under which the BIG-IP system should activate STARTTLS encryption for server-side traffic destined for a specific virtual server.
Creating a custom Client SSL profile
Creating a custom Server SSL profile
Creating a virtual server and load-balancing pool
You use this task to create a virtual server, as well as a default pool of LDAP servers. The virtual server then listens for and applies the configured STARTTLS activation to client-side or server-side LDAP traffic, or both. Part of creating this virtual server is specifying the names of any client-side and server-side LDAP and SSL profiles that you previously created.
Implementation result
After you have created the required LDAP and SSL profiles and assigned them to a virtual server, the BIG-IP® system listens for client- and server-side LDAP traffic on port 389. The BIG-IP system then activates the STARTTLS method for that traffic to provide SSL security on that same port, before forwarding the traffic on to the specified LDAP server pool.