Applies To:
Show Versions
BIG-IP AAM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP APM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP Link Controller
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP Analytics
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP LTM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP AFM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP PEM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP DNS
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP ASM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
Overview: Configuring the BIG-IP System for Passive Monitoring
You can configure a physical interface on a BIG-IP ®system to operate in passive mode. In this mode, the interface accepts mirrored traffic from another device to collect data for analysis and intrusion detection.
Passive mode behavior
The BIG-IP system analyzes the mirrored traffic, drops it, and then sends the resulting analytics data and log messages to a remote analytics and logging server. The mirrored traffic never leaves the system, and the BIG-IP system never acts on the headers and payload.
Benefits of passive monitoring
You don't need to deploy the BIG-IP system in line with your BIG-IP application delivery controller (ADC), which means there's no need to make changes to your network infrastructure.
Sample configuration
This illustration shows a configuration that includes a BIG-IP passive monitoring system.
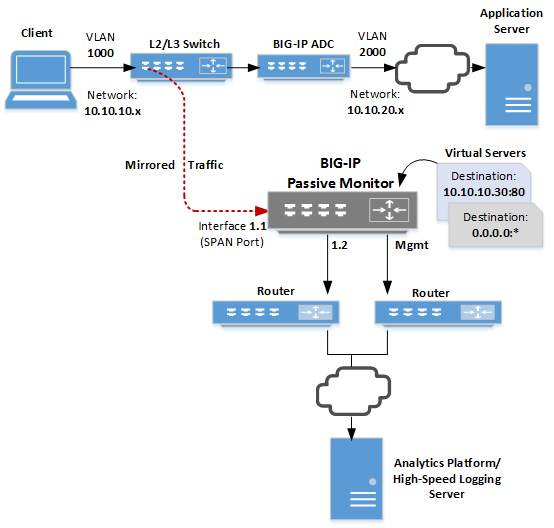
As we see in the illustration, a Layer 2/Layer 3 switch receives client traffic on the 10.10.10.x network. The traffic comes into the switch, which mirrors it to a SPAN port on the BIG-IP system. A SPAN port is an interface that can receive traffic mirrored to it from another device.
After analyzing the traffic, the BIG-IP system forwards all analytics data and log messages through interface 1.2 to a remote analytics and logging server and then discards its copy of the application traffic.
We've also configured two virtual servers to listen on the SPAN port. One virtual server listens for any mirrored HTTP traffic destined for a particular destination address on port 80, while the other listens for any traffic not caught by the HTTP virtual server.
Common use cases
Typical reasons for deploying a BIG-IP system as a passive monitoring device are:
- To collect HTTP analytics data
- To collect application analytics data along with Subscriber-awareness made available by BIG-IP Policy Enforcement Manager™ (PEM™)
- To enable firewall services that report on possible infringements
- To detect denial-of-service attacks with signaling to some external entity for triggering actions
- To perform intrusion detection services
- To perform behavioral analysis
Prerequisite configuration
Before you set up a BIG-IP system as a passive monitoring system, make sure you have configured these things:
- A network device, such as a Layer 2/Layer 3 switch, configured to receive client application traffic and mirror it to the BIG-IP passive monitoring system.
- A user account with a user role that grants permission to perform all tasks (Administrator, Resource Administrator, or Manager).
Other considerations
- A BIG-IP system operating in passive mode can accept mirrored traffic either raw or tunneled. In the case of tunneled traffic, the tunnel must be terminated on the BIG-IP system prior to the system analyzing the traffic.
- Global statistics do not differentiate between mirrored traffic and active traffic. However, statistics for an individual virtual server do differentiate between mirrored and active traffic because a virtual server applies to one type of traffic only.
- Passive mode is not available for interfaces on certain blade models.
- A trunk on which Link Aggregation Control Protocol (LACP) is enabled cannot operate as a passive monitoring interface.
- When you assign a passive monitoring interface to a BIG-IP VLAN, any self IP addresses associated with that VLAN will no longer respond to ARP requests.
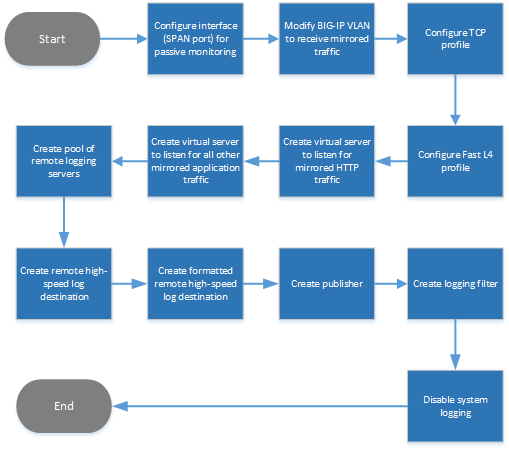
Task summary for passive monitoring
To configure the BIG-IP ® system to do passive monitoring, you designate an interface on the BIG-IP passive monitoring system as a SPAN port and assign the interface to the ingress VLAN. Then, you configure a Fast L4 profile to disable SYN cookie support and Packet Velocity® Asic (PVA) acceleration. Finally, you set up whatever virtual servers you need to listen for mirrored traffic.
The result is that the system will analyze ingress traffic and send log messages and analytics data to a remote analytics and high-speed logging server.
This illustration shows the order in which you need to perform these tasks.
Configure an interface for passive monitoring
Create a BIG-IP VLAN to accept mirrored traffic
Before performing this task, make sure that you have configured a VLAN with a tagged interface on the upstream switch that will mirror ingress application traffic and send it to this BIG-IP® system.
For any BIG-IP interface that you've configured to receive mirrored application traffic, you must create a VLAN and assign the interface to the VLAN.
Configure a TCP traffic filter for passive monitoring
You create a TCP profile to disable the SYN Challenge Handling setting.
- On the Main tab, click
- Click Create.
- In the Name field, type a name for the profile, such as my_tcp_profile.
- Scroll down to the Security and Quality of Service area of the screen, and on the right side, select the Custom check box.
- From the SYN Challenge Handling list, select Disable Challenges.
- At the bottom of the screen, click Finished.
Configure a Fast L4 traffic filter for passive monitoring
You create a Fast L4 profile to disable the Packet Velocity® ASIC settings and disable the SYN Challenge Handling setting.
Create a listener for mirrored HTTP traffic
Create a listener for non-specific mirrored traffic
Create a pool of remote logging servers
Create a remote high-speed log destination
You create a log destination of the Remote High-Speed Log type to specify that log messages are sent to a pool of remote log servers.
Create a formatted remote high-speed log destination
You create a formatted logging destination to specify that log messages are sent to a pool of remote log servers, such as Remote Syslog, Splunk, or ArcSight servers.





