Applies To:
Show Versions
BIG-IP AAM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP APM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP Link Controller
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP Analytics
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP LTM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP AFM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP PEM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP DNS
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP ASM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
BIG-IP system logging overview
Viewing and managing log messages is an important part of managing traffic on a network and maintaining a BIG-IP® system. Log messages inform you on a regular basis of the events that occur on the system.
Using the BIG-IP system’s high-speed logging mechanism, you can log events either locally on the BIG-IP system or remotely on a server. F5® Networks recommends that you store logs on a pool of remote logging servers.
For local logging, the high-speed logging mechanism stores the logs in either the Syslog or the MySQL database on the BIG-IP system, depending on a destination that you define.
Types of log messages
Examples of the types of messages that the high-speed logging mechanism can log are:
- BIG-IP® system-level events
- DNS events (for local traffic and global traffic)
- Network Firewall events
- Protocol Security events
- Carrier-grade NAT (CGNAT) events
- Denial-of-service (DoS) protection events
About existing Syslog configurations
If you previously configured the BIG-IP® system to log messages locally using the Syslog utility or remotely using the Syslog-ng utility, you can continue doing so with your current logging configuration, without configuring high-speed logging.
Alternatively, you can configure local Syslog logging using the high-speed logging mechanism, which is the recommended Syslog configuration. By configuring Syslog using high-speed logging, you can easily switch logging utilities in the future as needs change, without the need to perform significant re-configuration.
Remote storage of log messages
The way that you set up remote, high-speed logging is by first defining a pool of logging servers, and then creating an unformatted, remote high-speed log destination that references the pool. If you are using ArcSight, Splunk, or Remote Syslog logging servers that require a formatted destination, you can also create a formatted log destination for one of those server types. Once those objects are set up, you create a publisher and a custom logging profile pertaining to the type of message you want to log. You then assign the logging profile to a relevant virtual server, and the profile, in turn, references the publisher.
This image shows the BIG-IP® objects that you configure for remote high-speed logging. This figure shows the way that these objects reference one another from a configuration perspective.
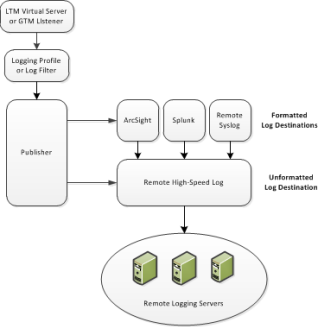
BIG-IP object referencing for remote high-speed logging
For an example of configuring remote, high-speed logging, suppose you want to send all Protocol Security messages to a group of remote ArcSight servers. In this case, you would create these objects:
- A load balancing pool for the ArcSight logging servers.
- An unformatted Remote High-Speed Log destination that references the pool of ArcSight logging servers.
- A formatted ArcSight log destination that references an unformatted log destination.
- A publisher that references the formatted and unformatted log destinations.
- A Protocol Security logging profile that references the publisher.
- An LTM® virtual server or DNS listener that references the logging profile and the load balancing pool.
- An unformatted Remote High-Speed Log destination that references the pool of ArcSight logging servers.
Local storage of log messages
Although F5® Networks does not recommend locally storing log messages, you can store log messages locally on the BIG-IP® system instead of remotely. In this case, you can still use the high-speed logging mechanism to store and view log messages locally on the BIG-IP system.
When you use the high-speed logging mechanism to configure local logging, the system stores the log messages in either the local Syslog data base or the local MySQL data base. The storage database that the BIG-IP system chooses depends on the specific log destination you assign to the publisher:
- local-syslog
- Causes the system to store log messages in the local Syslog database. When you choose this log destination, the BIG-IP Configuration utility displays the log messages in these categories: System, Local Traffic, Global Traffic, and Audit.
- local-db
- Causes the system to store log messages in the local MySQL database. When you choose local-db, the BIG-IP Configuration utility does not display the log messages.
About local Syslog logging
If you are using the Syslog utility for local logging, whether or not you are using the high-speed logging mechanism you can view and manage the log messages, using the BIG-IP® Configuration utility.
The local Syslog logs that the BIG-IP system can generate include several types of information. For example, some logs show a timestamp, host name, and service for each event. Moreover, logs sometimes include a status code, while the audit log shows a user name and a transaction ID corresponding to each configuration change. All logs contain a one-line description of each event.
For local log messages that the BIG-IP system stores in the local Syslog data base, the BIG-IP system automatically stores and displays log messages in these categories:
- System messages
- Packet filter messages
- Local Traffic messages
- Global Traffic messages
- BIG-IP system configuration (audit) messages
Each type of event is stored locally in a separate log file, and the information stored in each log file varies depending on the event type. All log files for these event types are in the directory /var/log.
Log level settings for BIG-IP system events
For each type of system-level process, such as bigdb configuration events or events related to HTTP compression, you can set a minimum log level. The minimum log level indicates the minimum severity level at which the BIG-IP® system logs that type of event. There are many different types of local traffic or global traffic events for which you can set a minimum log level.
The log levels that you can set on certain types of events, ordered from highest severity to lowest severity, are:
- Emergency
- Alert
- Critical
- Error
- Warning
- Notice
- Informational
- Debug
For example, if you set the minimum log level for bigdb events to Error, then the system only logs messages that have a severity of Error or higher for those events.
Logging system events
Many events that occur on the BIG-IP® system are Linux-related events, and do not specifically apply to the BIG-IP system. Using the BIG-IP Configuration utility, you can display these local system messages.
Logging packet filter events
Some of the events that the BIG-IP system logs are related to packet filtering. The system logs the messages for these events in the file /var/log/pktfilter.
Logging local traffic events
Many of the events that the BIG-IP system logs are related to local area traffic passing through the BIG-IP system. The BIG-IP system logs the messages for these events in the file /var/log/audit.
Code expansion in Syslog log messages
The BIG-IP® system log messages contain codes that provide information about the system. You can run the Linux command cat log |bigcodes |less at the command prompt to expand the codes in log messages to provide more information. For example:
Jun 14 14:28:03 sccp bcm56xxd [ 226 ] : 012c0012 : (Product=BIGIP Subset=BCM565XXD) : 6: 4.1 rx [ OK 171009 Bad 0 ] tx [ OK 171014 Bad 0 ]
About enabling and disabling auditing logging
An optional type of logging that you can enable is audit logging. Audit logging logs messages that pertain to actions that users or services take with respect to the BIG-IP® system configuration. This type of audit logging is known as MCP audit logging. Optionally, you can set up audit logging for any tmsh commands that users type on the command line.
For both MCP and tmsh audit logging, you can choose a log level. In this case, the log levels do not affect the severity of the log messages; instead, they affect the initiator of the audit event.
The log levels for MCP logging are:
- Disable
- This turns audit logging off. This is the default value.
- Enable
- This causes the system to log messages for user-initiated configuration changes only.
- Verbose
- This causes the system to log messages for user-initiated configuration changes and any loading of configuration data.
- Debug
- This causes the system to log messages for all user-initiated and system-initiated configuration changes.
The log levels for tmsh logging are:
- Disable
- This turns audit logging off.
- Enable
- This causes the system to log all tmsh commands, including commands that result in no change to the configuration. Note that the system does not generate a log entry when the user types the single command tmsh to open the tmsh shell. This is the default log level.
About remote logging using Syslog-ng
If you want to configure remote logging using Syslog-ng, you do not use the high-speed logging mechanism. Configuration of remote logging using Syslog-ng has some key differences compared to a remote, high-speed logging configuration:
- You do not configure log destinations, publishers, or a logging profile or log filter.
- Instead of creating a pool of remote logging servers (as you do with high-speed logging), you specify the IP addresses of the servers using the Remote Logging screen of the BIG-IP® Configuration utility.
- If you want to ensure that the Syslog-ng messages being logged remotely are encrypted, you must first establish a secure tunnel.





