Applies To:
Show Versions
BIG-IP LTM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0
Overview: Using NAPT address translation mode
NAPT mode provides standard address and port translation allowing multiple clients in a private network to access remote networks using the single IP address assigned to their router. For outbound packets, NAPT translates the source IP address and source transport identifier. For inbound packets, NAPT translates the destination IP address, the destination transport identifier, and the IP and transport header checksums. This mode is beneficial for remote access users.
Task summary
NAPT log examples
The following examples describe typical NAPT log messages
NAT44 example
Mar 27 11:17:39 10.10.10.200 lsn_event="LSN_ADD",cli="10.10.10.1: 33950",nat="5.5.5.1:10000" Mar 27 11:17:39 10.10.10.200 "LSN_ADD""10.10.10.1: 33950""5.5.5.1:10000" Mar 27 11:23:17 localhost info tmm[32683]: "LSN_ADD""10.10.10.1:33950""5.5.5.1:10000" Mar 27 11:17:39 10.10.10.200 lsn_event="LSN_DELETE",cli="10.10.10.1: 33950",nat="5.5.5.1:10000" Mar 27 11:17:39 10.10.10.200 "LSN_DELETE""10.10.10.1: 33950""5.5.5.1:10000" Mar 27 11:23:17 localhost info tmm[32683]: "LSN_DELETE""10.10.10.1:33950""5.5.5.1:10000"
NAT44 example with route domains
Mar 28 08:34:12 10.10.21.200 lsn_event="LSN_ADD",cli="10.10.10.1%11: 59187",nat="5.5.5.1%22:10000" Mar 28 08:34:12 10.10.21.200 "LSN_ADD""10.10.10.1%11: 59187""5.5.5.1%22:10000" Mar 28 08:34:12 10.10.21.200 lsn_event="LSN_DELETE",cli="10.10.10.1%11: 59187",nat="5.5.5.1%22:10000" Mar 28 08:34:12 10.10.21.200 "LSN_DELETE""10.10.10.1%11: 59187""5.5.5.1%22:10000"
NAT64 example
Mar 27 11:18:20 10.10.10.200 lsn_event="LSN_ADD",cli="2701: 1:12:123:1234:432:43:100.39900",nat="5.5.5.1:10000" Mar 27 11:18:20 10.10.10.200 "LSN_ADD""2701: 1:12:123:1234:432:43:100.39900""5.5.5.1:10000" Mar 27 11:23:57 localhost info tmm[32683]: "LSN_ADD""2701:1:12:123:1234:432:43:100.39900""5.5.5.1:10000" Mar 27 11:18:23 10.10.10.200 lsn_event="LSN_DELETE",cli="2701: 1:12:123:1234:432:43:100.39900",nat="5.5.5.1:10000" Mar 27 11:18:23 10.10.10.200 "LSN_DELETE""2701: 1:12:123:1234:432:43:100.39900""5.5.5.1:10000" Mar 27 11:24:00 localhost info tmm[32683]: "LSN_DELETE""2701:1:12:123:1234:432:43:100.39900""5.5.5.1:10000"
NAT64 example with route domains
Mar 28 14:50:56 10.10.21.200 lsn_event="LSN_ADD",cli="2701: 1:12:123:1234:432:43:100%11.45000",nat="5.5.5.1%22:10000" Mar 28 14:50:56 10.10.21.200 "LSN_ADD""2701: 1:12:123:1234:432:43:100%11.45000""5.5.5.1%22:10000" Mar 28 14:50:56 10.10.21.200 lsn_event="LSN_DELETE",cli="2701: 1:12:123:1234:432:43:100%11.45000",nat="5.5.5.1%22:10000" Mar 28 14:50:56 10.10.21.200 "LSN_DELETE""2701: 1:12:123:1234:432:43:100%11.45000""5.5.5.1%22:10000"
NAT DSLITE
Mar 27 11:19:14 10.10.10.200 lsn_event="LSN_ADD",cli="10.10.31.4: 52240",nat="5.5.5.1:10000",dslite="2701::200" Mar 27 11:19:14 10.10.10.200 "LSN_ADD""10.10.31.4: 52240""5.5.5.1:10000""2701::200" Mar 27 11:24:52 localhost info tmm[32682]: "LSN_ADD""10.10.31.4:52240""5.5.5.1:10000""2701::200" Mar 27 11:19:18 10.10.10.200 lsn_event="LSN_DELETE",cli="10.10.31.4: 52240",nat="5.5.5.1:10000",dslite="2701::200" Mar 27 11:19:18 10.10.10.200 "LSN_DELETE""10.10.31.4: 52240""5.5.5.1:10000""2701::200" Mar 27 11:24:55 localhost info tmm[32682]: "LSN_DELETE""10.10.31.4:52240""5.5.5.1:10000""2701::200"
NAT DSLITE with route domains
Mar 28 15:03:40 10.10.21.200 lsn_event="LSN_ADD",cli="10.10.31.4%11: 51942",nat="5.5.5.1%22:10000",dslite="2701::200%11" Mar 28 15:03:40 10.10.21.200 "LSN_ADD""10.10.31.4%11: 51942""5.5.5.1%22:10000""2701::200%11" Mar 28 15:03:40 10.10.21.200 lsn_event="LSN_DELETE",cli="10.10.31.4%11: 51942",nat="5.5.5.1%22:10000",dslite="2701::200%11" Mar 28 15:03:40 10.10.21.200 "LSN_DELETE""10.10.31.4%11: 51942""5.5.5.1%22:10000""2701::200%11"
NAPT log examples with timestamp
The following examples describe typical NAPT log messages with timestamp.
HSL raw messages example
"LSN_ADD""10.10.10.15:51326""TCP""5.5.5.0:80""1436465636143" "LSN_DELETE""10.10.10.15:51326""TCP""5.5.5.0:80""1436465636143""4" "LSN_ADD""10.10.10.15:51326""UDP""5.5.5.0:514""1436465636143" "LSN_DELETE""10.10.10.15:51326""UDP""5.5.5.0:514""1436465636143""4" "LSN_ADD""10.10.10.15:51326""ICMP""5.5.5.0:0""1436465636143" "LSN_DELETE""10.10.10.15:51326""ICMP""5.5.5.0:0""1436465636143""4"
Splunk raw messages example
ip_protocol="TCP",lsn_event="LSN_ADD",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:80" ip_protocol="TCP",lsn_event="LSN_DELETE",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:80",duration="4" ip_protocol="UDP",lsn_event="LSN_ADD",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:514" ip_protocol="UDP",lsn_event="LSN_DELETE",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:514",duration="4" ip_protocol="ICMP",lsn_event="LSN_ADD",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:0" ip_protocol="ICMP",lsn_event="LSN_DELETE",start="1436465636143", cli="10.10.10.15:51326",nat="5.5.5.0:0",duration="4"
remote-syslog raw messages (RFC3164 format) example
<134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_ADD""10.10.10.15:51326""TCP""4.4.0.0:80""1436465636143" <134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_DELETE""10.10.10.15:51326""TCP""4.4.0.0:80""1436465636143""4" <134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_ADD""10.10.10.15:51326""UDP""4.4.0.0:514""1436465636143" <134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_DELETE""10.10.10.15:51326""UDP""4.4.0.0:514""1436465636143""4" <134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_ADD""10.10.10.15:51326""ICMP""4.4.0.0:0""1436465636143" <134>Jul 09 11:13:56 victoria-5 tmm[11075]: "LSN_DELETE""10.10.10.15:51326""ICMP""4.4.0.0:0""1436465636143""4"
Local syslog raw messages
'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_ADD""10.10.10.15:51326""TCP""4.4.0.0:80""1436465636143"' 'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_DELETE""10.10.10.15:51326""TCP""4.4.0.0:80""1436465636143""4" 'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_ADD""10.10.10.15:51326""UDP""4.4.0.0:514""1436465636143"' 'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_DELETE""10.10.10.15:51326""UDP""4.4.0.0:514""1436465636143""4" 'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_ADD""10.10.10.15:51326""ICMP""4.4.0.0:0""1436465636143"' 'Jul 9 11:13:56 slot3/victoria-5 info tmm[11075]: "LSN_DELETE""10.10.10.15:51326""ICMP""4.4.0.0:0""1436465636143""4"
Creating a NAPT LSN pool
- The CGNAT module must be provisioned before LSN pools can be configured.
- Before associating a LSN pool with a log publisher, ensure that at least one log publisher exists on the BIG-IP system.
Creating a VLAN for NAT
Creating a NAT64 virtual server for an LSN pool
Overview: Using PBA mode to reduce CGNAT logging
Task summary
About PBA address translation mode
Port Block Allocation (PBA) mode provides you with the ability to log only the allocation and release of port blocks for a subscriber, instead of separately logging each network address translation (NAT) session as a separate translation event, as with network address and port translation (NAPT), thus reducing the number of log entries while maintaining legal mapping and reverse mapping requirements.
Restrictions
Configuration restrictions for PBA mode include these constraints.
- PBA mode is compatible only with SP-DAG. If a VLAN is used that is not compatible with SP-DAG, then NAPT mode becomes active and an error is logged.
- You can configure overlapping LSN prefixes only between pools of the same type. LSN prefixes are not overlapping when the port ranges for the prefixes do not overlap.
- The system allocates one primary port block for each subscriber, with the allocation of an additional overflow port block, as necessary.
- The Client Connection Limit value constrains the number of subscriber connections, preventing any one subscriber from using an excessive number of connections.
- PBA mode is available with NAT44, NAT64, and DS-Lite.
Behavior Characteristics
PBA mode manages connections by means of the following characteristics.
- Port allocation within an active port block occurs until all available ports become allocated, or until the Block Lifetime limit is exceeded.
- The Block Idle Timeout value specifies the period between when the last connection using a port block is freed and when the port block can be reused.
Reduced Logging
When you use PBA mode, a log entry is sent when a block of ports is allocated for a subscriber, and again when a block of ports is released. Log entries include the range of ports (that is, the port block) from the start port through the end port. Several logging destinations are available for PBA mode, including Syslog, Splunk, and IPFIX.
About configuring PBA mode with route domains
Port block allocation (PBA) mode can be used with route domains to configure multiple subscriber networks in separate route domains. You can also partition subscriber networks and the Internet by using route domains.
A route domain that is used for the translation entry is not the subscriber route domain. The subscriber route domain is, instead, applied to the egress interface.
In the following configuration, multiple subscribers can connect to servers in Internet route domain 0. The BIG-IP® system allocates, to each subscriber, available port blocks from Internet route domain 0 that include unique addresses and ports.
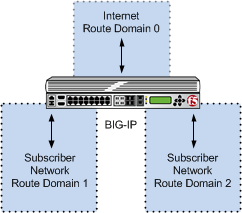
Multiple subscriber networks connecting to Internet servers in Internet Route Domain 0
In the next configuration, multiple subscribers can connect to servers in respective Internet route domains. The BIG-IP system allocates available port blocks from the respective Internet route domain to the corresponding subscriber. Allocated port blocks can differ only by route domain, and use identical address and port ranges; consequently, for this configuration, a service provider must provide a means to distinguish the connections of different route domains, as necessary.
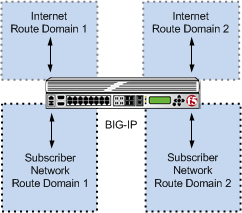
Multiple subscriber networks connecting to Internet servers in separate Internet route domains
PBA log examples
Following are some examples of the elements that comprise a typical Port Block Allocation (PBA) mode log entry.
NAT44 HSL example
PBA log messages include several elements of interest. The following examples show typical log messages, and the table describes common information types.
Jul 23 09:33:42 www.siterequest.com "LSN_PB_ALLOCATED""10.10.10.1""5.5.5.9: 5555-6666" Jul 23 09:33:42 www.siterequest.com "LSN_PB_RELEASED""10.10.10.1""5.5.5.9: 5555-6666"
Jul 23 09:33:42 www.siterequest.com "LSN_PB_ALLOCATED""10.10.10.1%55""5.5.5.9%22: 5555-6666" Jul 23 09:33:42 www.siterequest.com "LSN_PB_RELEASED""10.10.10.1%55""5.5.5.9%22: 5555-6666"
Jul 23 10:46:31 www.siterequest.com "LSN_PB_ALLOCATED""2701: :200""5.5.5.9:5555-6666" Jul 23 10:46:31 www.siterequest.com "LSN_PB_RELEASED""2701: :200""5.5.5.9:5555-6666"
Jul 23 09:36:33 www.siterequest.com "LSN_PB_ALLOCATED""2701: :200%11""5.5.5.9%22:5555-6666" Jul 23 09:36:33 www.siterequest.com "LSN_PB_RELEASED""2701: :200%11""5.5.5.9%22:5555-6666"
Jul 23 09:36:33 www.siterequest.com "LSN_PB_ALLOCATED""2701: :200""5.5.5.9:5555-6666" Jul 23 09:36:33 www.siterequest.com "LSN_PB_RELEASED""2701: :200"5.5.5.9:5555-6666"
Jul 23 09:36:33 www.siterequest.com "LSN_PB_ALLOCATED""2701: :200%33""5.5.5.9%22:5555-6666" Jul 23 09:36:33 www.siterequest.com "LSN_PB_RELEASED""2701: :200%33""5.5.5.9%22:5555-6666"
Jul 23 10:56:13 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_client="10.10.10.1",lsn_pb="5.5.5.9: 5555-6666" Jul 23 10:56:13 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_client="10.10.10.1",lsn_pb="5.5.5.9: 5555-6666"
Jul 23 10:56:13 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_client="10.10.10.1%55",lsn_pb="5.5.5.9%22: 5555-6666" Jul 23 10:56:13 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_client="10.10.10.1%55",lsn_pb="5.5.5.9%22: 5555-6666"
Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_dslite_client="2701: :200",lsn_pb="5.5.5.9:5555-6666" Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_dslite_client="2701: :200",lsn_pb="5.5.5.9:5555-6666"
Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_dslite_client="2701: :200%11",lsn_pb="5.5.5.9%22:5555-6666" Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_dslite_client="2701: :200%11",lsn_pb="5.5.5.9%22:5555-6666"
Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_client="2701: :200",lsn_pb="5.5.5.9:5555-6666" Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_client="2701: :200",lsn_pb="5.5.5.9:5555-6666"
Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_ALLOCATED",lsn_client="2701: :200%33",lsn_pb="5.5.5.9%22:5555-6666" Jul 23 10:57:08 www.siterequest.com lsn_event="LSN_PB_RELEASED",lsn_client="2701: :200%33",lsn_pb="5.5.5.9%22:5555-6666"
| Information Type | Example Value | Description |
|---|---|---|
| Timestamp | Jul 23 10:57:08 | Specifies the time and date that the system logged the event message. |
| Domain name | www.siterequest.com | Specifies the domain name of the client. |
| LSN event | lsn_event="LSN_PB_ALLOCATED"; lsn_event="LSN_PB_RELEASED" | Specifies the allocation or release of the port block.
Note:
|
| Client address | 10.10.10.1; 10.10.10.1%55; 2701: :200; 2701: :200%33; lsn_client="10.10.10.1"; lsn_client="10.10.10.1%55"; lsn_dslite_client="2701: :200"; lsn_dslite_client="2701: :200%11" | Specifies the address of the client. |
| Port block address | 5.5.5.9; 5.5.5.9%22 | Specifies the address of the port block. |
| Port range start | 5555 | Specifies the start of the port range. |
| Port range end | 6666 | Specifies the end of the port range. |
Creating a PBA LSN pool
- The CGNAT module must be provisioned before LSN pools can be configured.
- Before associating a LSN pool with a log publisher, ensure that at least one log publisher exists on the BIG-IP® system.
Creating a VLAN for NAT
Creating a virtual server for an LSN pool
Overview: Deterministic address translation mode
Deterministic address translation mode provides address translation that eliminates logging of every address mapping, while still allowing internal client address tracking using only an external address and port, and a destination address and port. Reverse mapping allows BIG-IP® CGNAT operators to respond to legal requests revealing the identity of the originator of a specific communication. A typical example is revealing the identity of file sharers or P2P network users accused of copyright theft.
Deterministic mode allows unique identification of internal client address based on:
- External address and port (the address and port visible to the destination server)
- Destination address and port (the service accessed by the client)
- Time
Restrictions
Deterministic mode has these configuration restrictions:
- Only NAT44 can use deterministic mode.
- The subscriber (client-side) and Internet (server-side) interfaces (VLANs) must be set either as a source or destination address in the CMP Hash setting.
- The complete set of all internal client addresses that will ever communicate through the
CGNAT must be entered at configuration time.Note: This means that all virtual servers referring to an LSN pool through deterministic NAT mode must specify the source attribute with a value other than 0.0.0.0/0 or ::/0 (any/0, any6/0).
- Use only the most specific address prefixes covering all customer addresses.
- Members of two or more deterministic LSN pools must not overlap; in other words, every external address used for deterministic mapping must occur in only one LSN pool.
- Deterministic mode does not support IPFIX.
Simplified logging
As an alternative to per-connection logging, deterministic mode maps internal addresses to external addresses algorithmically to calculate the mapping without relying on per-connection logging. Deterministic mode significantly reduces the logging burden while mapping a subscriber's inside IP address with an outside Internet address and port.
To decipher mapping generated by LSN pools using deterministic mode, you must use the DNAT utility that can be run from the system's tmsh command prompt.
Task summary
Creating a deterministic LSN pool
Creating a VLAN for NAT
Creating a virtual server for an LSN pool
Overview: The DNAT utility
BIG-IP® deterministic NAT (DNAT) mode allows conservation of log storage for service providers by mapping subscribers to public translation addresses and ports algorithmically so that very little data needs to be stored in logs. The DNAT utility (dnatutil) is necessary for identifying subscribers through calculation of reverse source address and port mapping of deterministic-mode LSN pools, by using the states stored in the log files.
The DNAT utility can interpret logs from version 11.4.0 and later, correctly reverse mapping subscribers, or forward mapping possible end-points of the subscriber. DNAT, as of version 11.5 of the BIG-IP system, supports multiple log destinations including, LTM®, Remote Syslog, and Splunk. The DNAT utility can parse logs from any supported DNAT log destination.
The DNAT utility binary can be run either on the BIG-IP system or on any supported Linux host. The DNAT utility package currently supports CentOS 64 and Ubuntu 64 for deployment on Linux systems to support reverse mappings on archived logs. The package is available from the F5® Downloads site (http://support.f5.com/kb/en-us.html).
Task summary
DNAT utility example commands
This list provides examples of the syntax used in commands for dnatutil.
| Command | Response |
|---|---|
| dnatutil 10.0.0.1 --action forward | Shows a list of translation address/port pairs that might be used for a subscriber at 10.0.0.1, using the DNAT states contained in /var/log/ltm. |
| dnatutil 173.240.102.139:5678 | Performs a reverse mapping back to the subscriber address for the connection from 173.240.102.139:5678, using the DNAT states contained in /var/log/ltm. |
| dnatutil --start_time ’2012-09-27 06:30:00’ --end_time ’2012-09-27 12:10:00’ 173.240.102.139:5678 | Performs a reverse mapping back to the subscriber address for the connection from 173.240.102.139:5678, but only shows the subscriber addresses that used the translation within the specified time range. |
| dnatutil --start_time ’2012-09-27 06:30:00’ --end_time ’2012-09-27 12:10:00’ --file ltmlog-21102013 173.240.102.139:5678 | Performs a reverse mapping back to the subscriber address for the connection from 173.240.102.139:5678, showing the subscriber addresses that used the translation within the specified time range, and using the DNAT states contained in /var/log/test. |
| dnatutil --file /var/log/test | Shows summary information, using the DNAT states contained in /var/log/test. |
| dnatutil --action summary --start_time ’2012-09-27 06:30:00’ --end_time ’2012-09-27 12:10:00’ | Shows summary information, using the DNAT states within the specified time range. |
| dnatutil --action reverse_addr 1.2.3.4 | Shows a list of possible subscriber addresses for the provided client address. |
| dnatutil --help | grep DAG_ID | Provides version information for the utility. |
Downloading the DNAT utility external tool
Using the DNAT utility external tool for reverse mappings
To discover the subscriber address, you need to have at least the NAT/public address you would like to translate. It is preferable to have the date, time, and NAT/public address, port, and the archived logs with the state information you wish to use.
Using DNAT utility to look up deterministic NAT mappings on the BIG-IP system
Overview: PCP client address translation
Port Control Protocol (PCP) clients can request specific NAT/CGNAT mappings for themselves and/or for third-party devices. This allows the PCP clients to set their own public-side IP addresses (also called translation addresses) in a network that uses CGNAT. In cases where the BIG-IP® system assigns a translation address or port other than the one requested, the client is at least aware of their assigned address or port.
You apply a PCP profile to a Large Scale NAT (LSN) pool of translation addresses. A client that uses the LSN pool can also send PCP requests to the BIG-IP system to request a particular address/port from the pool. RFC 6887 defines PCP.
Task summary
Creating a PCP profile
Configuring an LSN pool with a PCP profile
You assign a PCP profile to an LSN pool in the pool's configuration screen. You also designate the IP address and/or DS-Lite tunnel to which the virtual server's clients can send their PCP requests.





