Applies To:
Show Versions
BIG-IP APM
- 14.0.0, 13.1.1, 13.1.0, 13.0.1, 13.0.0, 12.1.3, 11.6.3, 11.5.7
Configuring Per-App VPN with APM and F5 Access
What is per-app VPN?
Apple's Network Extension framework supports layer-3 tunneling for both device-wide and Per-App VPN tunnels. This means that TCP and UDP protocols are supported for apps configured for Per-App VPN on F5 Access for iOS 2018. Apps that are managed by a Mobile Device Manager (MDM) can be configured to automatically connect to a VPN when they are started. In addition, Mobile Safari can be managed for per-app VPN with a configuration profile and without an MDM. Per-app VPN gives IT granular control over corporate network access, and ensures that data transmitted by managed apps travels only through a VPN. Meanwhile, other data, like an employee's personal web browsing activity, does not use the VPN. Per-app VPN also works with Safari on a per-URL basis.
A per-app VPN configuration requires three configuration components.
- A device under MDM management, or a configuration profile file installed manually. For more information, see Configuration Profile Reference.
- A managed app installed on the device, or Mobile Safari.
- F5 Access for iOS installed on the managed device.
About deploying MDM apps over VPNs
The per-app VPN framework allows the administrator to limit VPN access to explicit apps only. Specifically, it allows applications to use one F5 Access configuration (or VPN connection).
In practice, some applications may be associated with one F5 Access configuration, and other applications may be associated with other F5 Access configurations.
In this example, App 1 or App 2 can be active at the same time, because they use different VPN configurations.
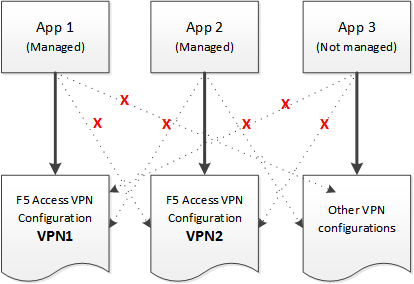
Apps associated with different VPN configurations
Creating an access profile
Adding a version check to the access policy
Adding a client certificate check to the access policy
About setting up Access Policy Manager for per-app VPN
You configure specific settings in the Access Policy Manager® to provide per-app VPN tunnels. Per-app VPN tunnels are full network access tunnels, and require Network Access resources in the Access Policy. Configure these items on the Access Policy Manager.
- The virtual server must be configured with an access profile.
- The virtual server should be configured with a basic configuration for the network access resource.
- You must specify the Client SSL profile on the virtual server. You must also include the same CA bundle on the server that is used to generate the certificate for the client devices.
Configuring a virtual server for per-app VPN
A virtual server profile enables support for the network access used by per-app VPN tunnels.





