Applies To:
Show Versions
BIG-IP APM
- 14.0.0, 13.1.1, 13.1.0, 13.0.1, 13.0.0, 12.1.3, 11.6.3, 11.5.7
Overview: F5 Access for iOS
Introducing F5 Access 2018
F5 Access for iOS 2018 is a new client, built on the latest Apple VPN architecture. Apple's new Network Extension architecture allows for some features that were not previously included in our iOS client, including the ability to use UDP apps with Per-App VPN. Apple has deprecated their previous VPN technology, which will not be supported in the future, so our previous clients based on older technology will eventually be deprecated as well.
This is not a one-to-one upgrade from the previous version (F5 Access 2.x). A number of incompatibilities, possible incompatibilities, and configuration changes are outlined in this document that may affect your migration to F5 Access for iOS 2018. MDM support for this new client is still in development. Please check with your MDM vendor for more information.
There are access policy changes required to support this client. If you are planning to migrate users to the new client, please review all of the differences between the clients outlined in this document before you migrate your users. We expect to add features and to support to this client in the future, and eventually we expect the same level of support from MDM vendors with our existing client.
Differences between F5 Access 2018 and F5 Access 2.1.x
There are a number of differences between F5 Access 2018 and F5 Access 2.1.x.
Configuration deployment changes
When deploying configurations, there are several differences between F5 Access 2.1.x and F5 Access 2018.
| VPN type | Manually configured | MDM configured |
|---|---|---|
| Device-wide VPN |
No user-side Client Certificate import User has to accept a permission dialog to add the first VPN configuration |
The key VPNSubType has changed.
|
| Per-App VPN | No manual configuration |
|
Device UDID change
Device UDID is no longer provided, due to iOS changes. With an MDM, the device can be assigned an ID. This is assigned with the MdmDeviceUniqueId or UDID attribute. This assigned value populates the session variables session.client.mdm_device_unique_id and session.client.unique_id. If neither is provided this session variable is not present. If either field is provided by the MDM, both session variables are present. An example value is RC1KQLCJFOJEEM0XIOB3P52OMUQ3UN9Y3SDA5RWR.VPN establishment changes
When establishing VPNs, there are several differences between F5 Access 2.1.x and F5 Access 2018.
| VPN type | Manual | On-demand |
|---|---|---|
| Device-wide VPN |
|
In F5 Access 2018, notifications must be enabled for any user
prompts or Web Logon interactions. With notifications enabled, these
prompts and features are supported.
|
| Per-App VPN | No manual configuration | A Per-App VPN connection cannot be established if user interaction is required. For F5 Access 2018, configure the access policy so user interaction is not required to establish the VPN connection. |
Access Policy Manager configuration changes
When configuring Access Policy Manager, there are several differences between F5 Access 2.1.x and F5 Access 2018.
| APM configuration item | Change |
|---|---|
| Enforce Logon Mode | In the Connectivity Profile, the administrator can now enforce a specific logon mode, using the setting Enforce Logon Mode. The logon mode can be enforced as native or web. |
| Web Logon mode in F5 Acesss for iOS app | If Enforce Logon Mode is enabled in the Connectivity Profile, the user cannot change the Web Logon option. |
| Per-App VPN configuration item | Change |
|---|---|
| Virtual Server | In the Virtual Server configuration, the option Application Tunnels (Java & Per-App VPN) is no longer required to be enabled |
| Access policy | With F5 Access 2018, Per-App VPN now uses an L3 tunnel. As such,
the following items must be added to the applicable access policy branch:
|
| iOS device | The iOS device enforces the applications that are allowed to access the VPN, according to the Per-App VPN configuration. |
Apple App Transport Security (ATS) changes
Apple Transport Security (ATS), implemented in F5 Access 2018, requires the following security changes for communications between F5 Access 2018 and the corresponding BIG-IP.
- Plain text HTTP connections are no longer allowed.
- HTTPS requires the strongest TLS configuration (TLS 1.2 and PFS cipher suites).
- Self-signed certificates are not supported unless the CA certificate is first Trusted on the device.
Client Certificate authentication
Client Certificate Authentication is not supported in Web Logon mode.
F5 Access and mobile devices
F5 Access for mobile devices provides full network access through BIG-IP® Access Policy Manager® . With network access, users can run applications such as RDP, SSH, Citrix, VMware View, and other enterprise applications on their mobile devices.
For information about how to use F5 Access on your device, refer to the F5 Access for iOS User Guide.
- N-factor authentication (at least two input fields, password and passcode) support
- User name and password, client certificate, and RSA SecurID support
- Multiple input field support
- Credential caching support
- Support for TouchID authentication, PIN, or a device password to make a connection, when using cached credentials
- Support for DNS address space for split-tunneling configurations
- Support for checking information from client devices
- Support for automatically launching applications on client devices
- Support for roaming between cellular and WiFi networks
- Landing URI support
- Logging support to report issues
- Support for private-side internal proxy servers. Public-side proxy servers are not currently supported.
- Per-app VPN support for TCP and UDP applications
- Application notifications
- Diagnostics
- Traffic Graphs
- Support for SAML 2.0 features in BIG-IP®Access Policy Manager®
- iOS widget support
About app notifications
F5 Access for iOS 2018 requires that notifications be enabled for most user configurations. This requires that the app be started by the user and accept notifications.
About SAML support
- Service provider-initiated access only, for example, APM acting as the service provider (SP)
- Web Logon mode only
- Single Log-Out (SLO): supported only when the logout action is initiated from the client
When you use F5 Access as a client performing SP-initiated access, F5 Access first connects to BIG-IP® Access Policy Manager® (APM®). Because there is no assertion, APM redirects the client to the IdP. The IdP then authenticates the user and redirects F5 Access back to the SP with assertion. APM then accepts the assertion and establishes a VPN connection. You can then access back-end resources through >F5 Access.
You can configure a BIG-IP system by configuring APM as an SP. The access policy that is associated with the configuration assigns a SAML AAA resource followed by a Network Access Resource. For more information about SAML configurations, refer to the BIG-IP® Access Policy Manager®: Authentication and Single Sign-On guide.
About supported authentication types
| Authentication type | Connection type |
|---|---|
| Username and password | Runtime prompts (login dialogs, device authentication, and other user input
prompts) are allowed for:
|
| Client certificate |
Note: A client certificate can only be installed by an MDM, or with a
.mobileconfig file.
|
| Client certificate + username and password |
Runtime prompts (login dialogs, device authentication, and other user input prompts) are allowed for:
For a Per-App VPN connection, runtime prompts are not supported, so the username and password must be specified in the configuration. Per-App VPN does not support Web Logon mode.
Note: A client certificate can only be installed by an MDM, or with a
.mobileconfig file.
|
About establishing VPN connections
The F5 Access application (app) for mobile devices provides users with two options to establish a VPN tunnel connection. A user can start a tunnel connection explicitly with the F5 Access application, or implicitly through the VPN On-Demand functionality.
For example, a connection can be configured to automatically trigger whenever a certain domain or host name pattern is matched.
For Per-App VPN, the following on demand considerations apply. These do not apply to On-Demand device-wide VPN connections.
- When a Per-App VPN connection is initiated On-Demand, user intervention is not allowed. For example, if a password is needed for authentication, but is not supplied in the configuration, the connection fails. Note that RSA authentication is not supported.
- On-Demand Per-App VPN does not work with Web Logon.
About pre-logon checks supported for iOS devices
Access Policy Manager® can check unique identifying information from an iOS client device. The supported session variables, which become populated with the iOS client device information, are gathered automatically, and can easily be combined with an LDAP or AD query to implement white-listing in a custom action to improve access context. This information allows Access Policy Manager to perform pre-logon sequence checks and actions based on information about the connecting device. Using such information, Access Policy Manager can perform the following tasks:
- Deny access if the iOS version is less than the required level.
- Deny access if the app version is less than required.
This example displays an access policy with a custom action to check the app version.
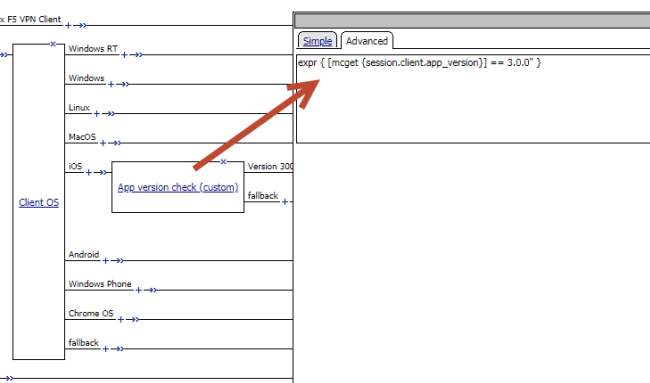
Example of a custom action for checking the F5 Access app version
About automatically launching applications from mobile devices
You can configure F5 Access to launch an app with a registered URL scheme after a VPN connection is established.
Auto-launching applications from F5 Access
About network integration on iOS devices
Access Policy Manager® provides web application-level security to prevent malware attacks. As an administrator, you can enforce all web access through a secured gateway, as well as bypass secure gateways for internal resources. This is especially helpful, for example, when you have clients using corporate tablets, smartphones, or other mobile devices to browse the web.
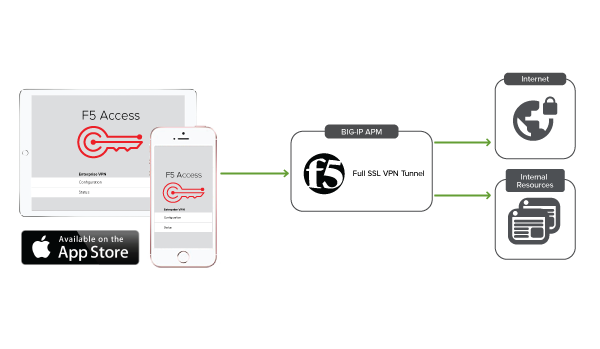
Setting up network access
Prerequisites for configuring F5 Access
Before configuring F5 Access for iOS devices, you must complete the following requirements:
- Set up BIG-IP® Access Policy Manager®.
- Run the Network Access Setup Wizard.





