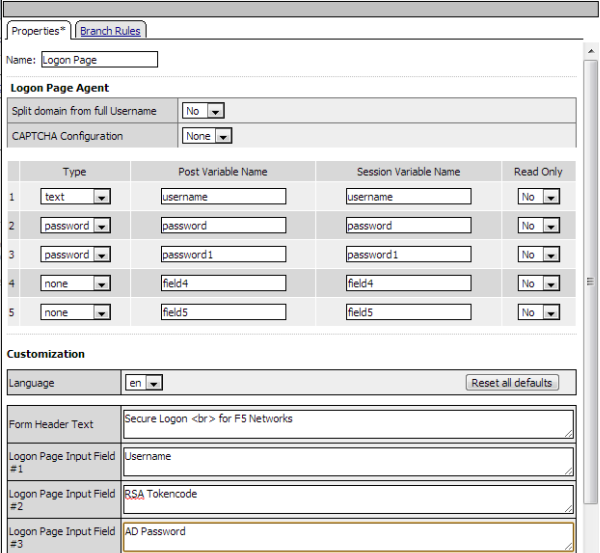
Applies To:
Show Versions
BIG-IP APM
- 12.0.0
Integrating APM with a Citrix Web Interface Site
Overview: Integrating APM with Citrix Web Interface sites
In this implementation, Access Policy Manager® performs authentication while integrating with a Citrix Web Interface site. The Web Interface site communicates with the XenApp server, renders the user interface, and displays the applications to the client.
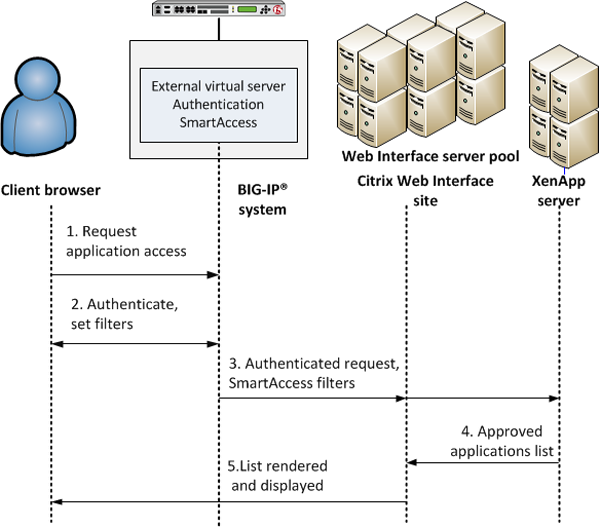
APM Citrix Web Interface integration with SmartAccess support
The preceding figure shows a configuration with one virtual server that communicates with clients and the Web Interface site.
- A user (client browser or Citrix Receiver) requests access to applications or features.
- The external virtual server starts an access policy that performs authentication and sets SmartAccess filters.
- The external virtual server sends the authenticated request and filters to the Citrix Web Interface site. The Citrix Web Interface site, in turn, forwards the information to the XML broker (XenApp server).
- The XML Broker returns a list of allowed applications to the Citrix Web Interface site.
- The Citrix Web Interface site renders and displays the UI to the user.
In cases where the Web Interface site cannot communicate with an external virtual server, you must configure an additional, internal, virtual server to manage requests from the Citrix Web Interface as part of Smart Access and SSO. You need an internal virtual server, for example, when the Web Interface site is behind a firewall, uses HTTP in the Authentication URL, or uses a different SSL CA certificate for establishing trust with APM than the one used by client devices.
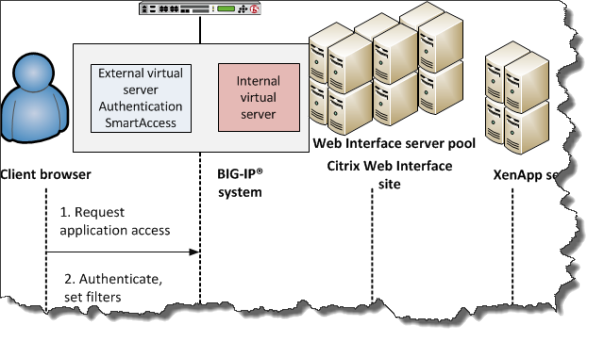
Internal virtual server for requests from Web Interface site
Supported clients
This implementation supports web clients and Citrix Receiver (iOS, Android, Mac, Windows, and Linux) clients.
Supported authentication
For Citrix Receiver Windows and Linux clients: only Active Directory authentication is supported.
For Citrix Receiver clients for iOS, Android, and Mac: Active Directory, or both RSA and Active Directory authentication is supported.
For web clients, you are not restricted in the type of authentication you use.
About the iApp for Citrix integration with APM
An iApps® template is available for configuring Access Policy Manager® and Local Traffic Manager™ to integrate with Citrix applications. The template can be used on the BIG-IP® system to create an application service that is capable of performing complex configurations. You can download the template from the F5® DevCentral™ iApp Codeshare wiki at https://devcentral.f5.com/wiki/iApp.Citrix-Applications.ashx. A deployment guide is also available there.
Task summary for APM integration with Citrix Web Interface sites
Ensure that you configure the Citrix components in the Citrix environment, in addition to configuring the BIG-IP® system to integrate with Citrix Web Interface sites.
Perform these tasks on the BIG-IP system to integrate Access Policy Manager® with a Citrix Web Interface site.
Task list
Creating an access profile
Verifying log settings for the access profile
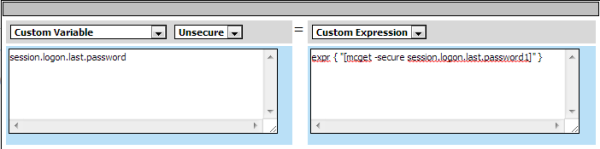
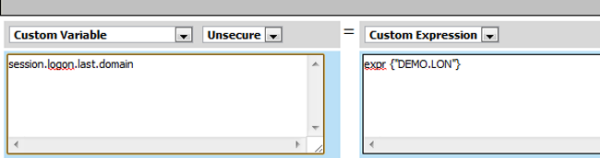
Creating an access policy for Citrix SSO
You should have an access policy that resembles one of these examples:
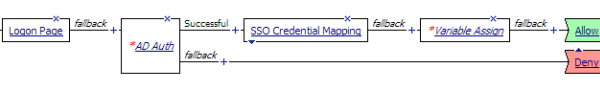
Example access policy with AD authentication, credential mapping, and Web Interface site domain assignment
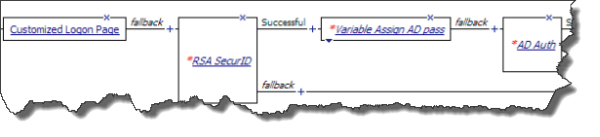
Configuring RSA SecurID authentication before AD authentication
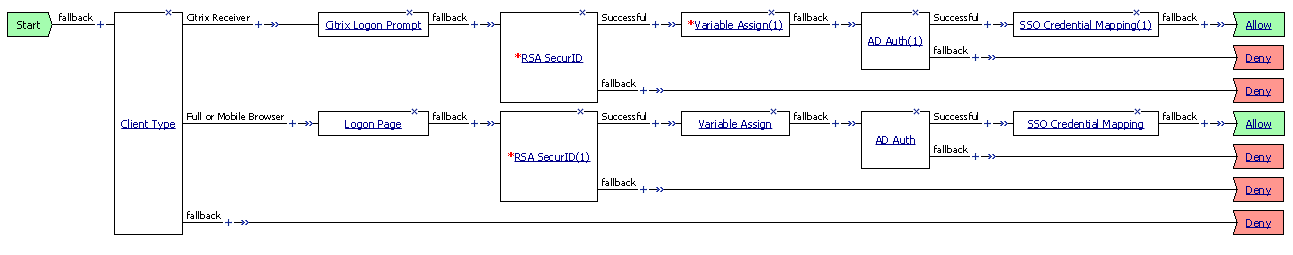
Example access policy with Citrix Logon Prompt
Adding Citrix Smart Access actions to an access policy
Example access policy with Citrix SmartAccess filters
Here is a typical example access policy that uses Citrix SmartAccess filters to restrict access to published applications based on the result of client inspection. Client inspection can be as simple as IP Geolocation Match or Antivirus. The figure shows an access policy being configured with a Citrix Smart Access action to set a filter to antivirus after an antivirus check is successful.
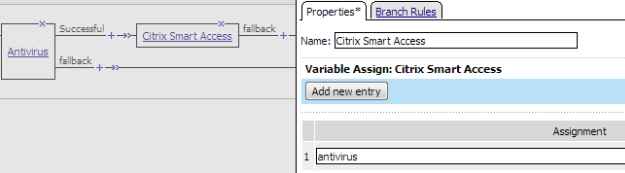
Example access policy with Citrix SmartAccess action and an antivirus check