Before you can create this access policy, configure the AAA server (or servers) to
use for authentication.
Note: The View Client supports authentication with
Active Directory domain credentials (required) and with an RSA SecureID PIN
(optional). To use both types of authentication, place the Active Directory logon
and authentication actions after the RSA logon and authentication actions.
Create an access policy so that a View Client can use a View desktop after logging
on and authenticating with Access Policy Manager (APM).
-
On the Main tab, click .
The Access Profiles List screen opens.
-
In the Access Policy column, click the Edit link for the
access profile you want to configure.
The visual policy editor opens the access policy in a separate
screen.
-
Click the (+) icon anywhere in the access policy to add
a new action item.
A popup screen opens, listing predefined actions on tabs such as General
Purpose, Authentication, and so on.
-
Type client in the search field, select
Client Type from the results list, and click
Add Item.
The Client Type action identifies clients and enables branching based on the
client type.
A properties screen opens.
-
Click Save.
The properties screen closes. The visual policy editor displays the
Client Type action. A VMware View branch follows it. Add the remaining actions
on the VMware View branch.
-
Configure logon and authentication actions for Active Directory:
Active Directory authentication is required.
-
Click the (+) sign on the VMware View branch. An
Add Item screen opens, listing predefined actions on tabs such as
General Purpose, Authentication, and so on
-
On the Logon tab, select VMware View Logon Page,
and click Add Item.
A properties screen displays.
-
From the VMware View Logon Screen Type list,
retain the default setting Windows
Password.
-
In the VMware View Windows Domains field, type
domain names separated by spaces to use for Active Directory
authentication.
Type at least one domain name. These domains names are displayed on
the View Client.
-
Click Save.
The properties screen closes and the visual policy editor is
displayed.
-
Click the plus (+) icon after the previous
VMware View Logon Page action.
A popup screen opens.
-
On the Authentication tab, select AD
Auth, and click Add Item.
-
From the Server list, select an AAA server and
click Save.
The properties screen closes.
-
Assign a full webtop and the VMware View remote desktop resource that you
configured previously.
-
Click the (+) sign after the previous
action.
-
Type adv in the search field, select
Advanced Resource Assignment from the
results, and click Add Item.
A properties screen displays.
-
Click Add new entry
A new line is added to the list of entries.
-
Click the Add/Delete link below the entry.
The screen changes to display resources on multiple
tabs.
-
On the Remote Desktop tab, select the VMware View remote desktop
resource that you configured previously.
-
On the Webtop tab, select a full webtop and click
Update.
The properties screen closes and the resources you selected are
displayed.
-
Click Save.
The properties screen closes and the visual policy editor is
displayed.
-
To use RSA SecurID authentication in addition to Active Directory
authentication, insert logon and authentication actions for RSA SecurID ahead of
those for Active Directory:
-
Click the (+) sign before the previous VMware
View Logon Page action.
A popup screen opens.
-
On the Logon tab, select VMware View Logon Page,
and click Add Item.
A properties screen displays.
-
From the VMware View Logon Screen Type list,
select RSA SecurID.
-
In the VMware View Windows Domains field, type
the domain names to use for logon.
-
Click Save.
The properties screen closes and the visual policy editor is
displayed.
-
Click the plus (+) icon after the previous
VMware View Logon Page action.
A popup screen opens.
-
On the Authentication tab, select RSA
SecurID, and click Add
Item.
-
From the Server list, select the AAA server that
you created previously and click Save.
The properties screen closes.
-
Optional:
If you want to display a message to the user inside of the View Client (for
example, a disclaimer or acceptable terms of use), this is how you do it:
-
Click the (+) icon anywhere in your access
profile to add a new action item.
An popup screen opens, listing predefined actions on tabs such
as General Purpose, Authentication, and so on.
-
On the Logon tab, select VMware View Logon Page,
and click Add Item.
A properties screen displays.
-
From VMware View Logon Screen Type, select
Disclaimer
-
In the Customization area from the Language
list, select the language for the message.
-
In the Disclaimer message field, type the
message to display on the logon page.
-
Click Save.
The properties screen closes and the visual policy editor is
displayed.
You have configured a logon page that displays a logon page with a
message on a View Client.
-
On the fallback branch between the last action and Deny,
select the Deny check box, click
Allow, and click Save.
-
Click Apply Access Policy.
You have an access policy that displays at least one logon page, and authenticates a
View Client against Active Directory before assigning resources to the session; and
at most, displays three logon pages and performs two-factor authentication before
assigning resources to the session.
 Example access policy with single-factor authentication for View Client
Example access policy with single-factor authentication for View Client
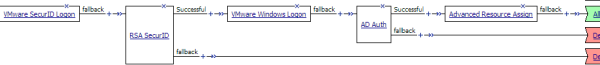 Example access policy with two-factor authentication for View Client
Example access policy with two-factor authentication for View Client
For the access policy to take effect, you must add it to a virtual
server.

 Example access policy with single-factor authentication for View Client
Example access policy with single-factor authentication for View Client
 Example access policy with two-factor authentication for View Client
Example access policy with two-factor authentication for View Client





