Applies To:
Show Versions
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1, 12.1.0
Kerberos Authentication for SWG Forward Proxy
Overview: Authenticating SWG users with Kerberos
You can include authentication in the access policy in a Secure Web Gateway (SWG) explicit or transparent forward proxy configuration. However, if the first site that a user accesses uses HTTP instead of secure HTTP, passwords are passed as clear text. To prevent this from happening, F5® recommends using Kerberos or NTLM authentication.
To use Kerberos authentication with SWG, if you do not already have Kerberos authentication configured and working with Access Policy Manager®, complete these tasks before you configure access policies for SWG.
Task summary
About basic authentication and Kerberos end-user logon
Access Policy Manager® (APM®) provides an alternative to the form-based login authentication method. Instead, an HTTP 401 (unauthorized) or HTTP 407 (proxy authentication required) response triggers a browser login screen to collect credentials.
This option is useful when a user is already logged in to the local domain and you want to avoid submitting an APM HTTP form for collecting user credentials. The browser automatically submits credentials to the server and bypasses the login box to collect the credentials again.
The benefits of this feature include:
- Provides flexible login mechanism instead of restricting you to use only the form-based login method.
- Eliminates the need for domain users to explicitly type login information again to log in to APM.
- Eliminates the need for user password transmission with Kerberos method.
How does end-user logon work?
To retrieve user credentials for end-user logon, you can use the basic authentication method, or the SPNEGO/Kerberos method (which is recommended), or both.
- Basic authentication
- Use this method to retrieve user credentials (user name and password) from a browser. You
can think of this method as a replacement for form-based authentication used by the standard
login screen. If you use basic authentication, Access Policy Manager® (APM®) populates the user name and password session variables, which can then
be used by any other authentication actions, such as Active Directory or RADIUS.Note: When using basic authentication, passwords are passed as clear text.
- SPNEGO/Kerberos
- Use this method to retrieve user credentials through the SPNEGO/Kerberos authentication
header. With the Kerberos method, the client system must first join a domain. A Kerberos action
does not run immediately; it runs only when the server requests SPNEGO/Kerberos authentication.
By default, Kerberos authentication runs not only on the first request, but also on subsequent
requests where authentication is needed, such as for new connections. APM validates the request
by confirming that a valid ticket is present. Note: You can disable Kerberos per request-based authentication in the AAA Kerberos authentication access policy item configuration in APM. If you disable it, authentication occurs while the access policy runs and subsequent authentications do not occur.
Both methods require that either an HTTP 401 Response (unauthorized) or an HTTP 407 Response (proxy authentication required) action item be configured in the access policy, and that the authentication method (basic, negotiate, or basic + negotiate) be specified in the action item.
In cases where both methods (basic + negotiate) are selected, the browser determines which method to perform based on whether the system has joined a domain. The HTTP 401 Response and HTTP 407 Response actions each have two default branches to indicate whether basic authentication or Kerberos method is performed.
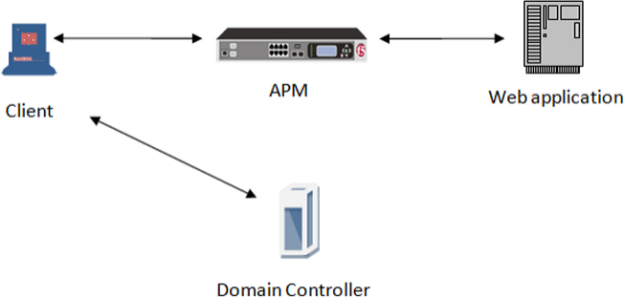
How SPNEGO/Kerberos end-user login works
The end-user logon works with events happening in this order:
- The client becomes a member and connects to the domain.
- The client connects to a virtual server on the BIG-IP® system.
- The access policy runs and issues a 401 or 407 HTTP response.
- If a Kerberos ticket is present or can be obtained, the browser forwards the Kerberos ticket along with the request when it receives the 401 or 407 response.
- APM validates the Kerberos ticket after the request is received, and determines whether or not to permit the request.
About Kerberos authentication requirements
To configure Kerberos authentication, you must meet specific configuration requirements as described here.
- Virtual server
- The virtual server IP address and host name are necessary to configure DNS.
- DNS configuration
- Make sure you have the zone file and PTR record for the virtual server IP address. For
example:
testbed.lab.companynet 10.10.4.100
- Browser configuration
- Configure the browser to use Kerberos. Typically, Internet Explorer is already configured for Kerberos; however, you might need to configure it for trusted sites. To use Firefox, you must configure it for negotiate authentication.
Joining a Kerberos user account to a domain
Configuring an AAA server for Kerberos authentication
Kerberos authentication troubleshooting tips
You might choose to verify Kerberos authentication configurations in some instances. Use these troubleshooting tips to help resolve any issues you might encounter.
Verify the keytab file
From the command line, use the klist command as shown in this example.
klist -ke WRFILE:/config/filestore/files_d/Common_d/kerberos_keytab_file_d/\:Common\:SUN-SPNEGO-APM106_key_file_2
The output for the example contains information like this.
Keytab name:
FILE:/config/filestore/files_d/Common_d/kerberos_keytab_file_d/:Common:SUN-SPNEGO-APM106_key_file_2
KVNO Principal
3 HTTP/apm106.labt.companynet.com@labt.companynet.com(arcfour-hmac)
Verify Kerberos delegation
kinit HTTP/apm106.labt.companynet.com@labt.companynet.comYou are prompted for a password and should receive a ticket (no output, no error).
Verify ticket
From the command line, type klist . Here is sample output: /etc/krb5.conf
Capture a TCP dump
Make sure the client sends the ticket to the BIG-IP® system; this verifies that the client setup is successful.
Implementation result
You should have a domain-joined user account for Kerberos and an AAA Kerberos server configured in Access Policy Manager®.





