Applies To:
Show Versions
BIG-IP APM
- 11.5.10, 11.5.9, 11.5.8, 11.5.7, 11.5.6, 11.5.5, 11.5.4, 11.5.3, 11.5.2, 11.5.1
About user identification
Secure Web Gateway (SWG) identifies users and maps them to IP addresses, or to sessions, without using cookies. Based on user identity, SWG assigns the appropriate scheme to each user. A scheme categorizes and filters URLs.
About session management cookies and Secure Web Gateway
Secure Web Gateway (SWG) does not use Access Policy Manager® (APM®) session management cookies. If presented with an APM session management cookie, SWG ignores it.
About ways to configure user identification for SWG
User identification configuration requires a method setting in the access profile and an access policy configured to support the setting. Based on user identification, you can determine which scheme to assign in the access policy so that Secure Web Gateway (SWG) filters URLs appropriately.
Depending on the access profile type, you can select one of these user identification methods: by IP address (for SWG-Explicit or SWG-Transparent access profile types) or by credentials (for SWG-Explicit type).
Identification by IP address
When you identify users by IP address, you can employ any of these methods.
- transparent user identification
- Transparent user identification makes a best effort to identify users without requesting
credentials. It queries domain controllers and stores a mapping of IP addresses to user
names in an IF-MAP server. Note: To identify users transparently, you must first install and configure the F5® DC Agent.
- explicit user identification
- You can present a logon page in an access policy to request user credentials and validate them. SWG maintains an internal mapping of IP addresses to user names. (You can present the appropriate logon page for the access policy type. For explicit forward proxy, you can present a 407 page. For transparent forward proxy, you can present a 401 page.)
- source IP ranges or subnets
- You can forego actually identifying the user and base the choice of which scheme to apply on whether the IP address is in a source IP range or on a subnet. SWG maintains an internal mapping of IP addresses to sessions.
- single scheme
- You can apply the same scheme to all users. SWG maintains an internal mapping of IP addresses to sessions.
Identification by credentials
When you choose to identify users by credentials, SWG maintains an internal mapping of credentials to sessions. To support this choice, you need an NTLM Auth Configuration object and you should check the result of NTLM authentication in the access policy.
Overview: Identifying users transparently
The F5® DC Agent enables transparent user identification, a best effort to identify users without requesting credentials.
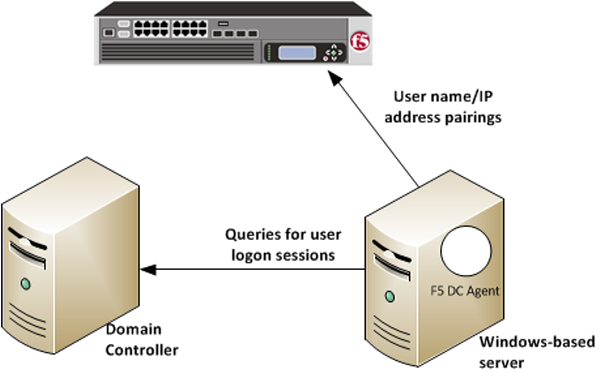 How F5 DC Agent transparently identifies users
How F5 DC Agent transparently identifies users
You can install the F5® DC Agent on a Windows-based server in any domain in the network. The F5 DC Agent discovers domains and domain controllers, queries the domain controllers for logon sessions, and sends an IP-address-to-user-name mapping to the BIG-IP® system. F5 DC Agent sends only those new user name and IP address pairs recorded since the previous query. The BIG-IP system maintains user identity information in an IF-MAP server and stores only the most recently identified user name for a given IP address.
Considerations for installing multiple agents
You can install more than one F5 DC Agent in your network and configure F5 DC Agents to communicate with the same BIG-IP system.
- NetBIOS port 139
- F5 DC Agent uses NetBIOS port 139 for automatic domain detection. If NetBIOS port 139 is blocked in your network, you can deploy an F5 DC Agent instance for each virtually or physically remote domain.
- Multiple subnets
- As a best practice, install a separate F5 DC Agent in each subnet to avoid problems gathering logon information from domain controllers.
- Network size, disk space, and RAM
- If your network is very large (10,000+ users or 30+ domain controllers), you might benefit from installing F5 DC Agent on multiple machines to evenly distribute resource usage. F5 DC Agent uses TCP to transmit data, and transmits roughly 80 bytes per user name and IP address pair.
| Number of users | Average amount of data transferred per day |
|---|---|
| 250 users | 30 KB |
| 2,000 users | 240 KB |
| 10,000 users | 1200 KB |
Task summary
Configuring the BIG-IP system for the F5 DC Agent
Verifying network communication
Downloading and installing F5 DC Agent
Updating privileges for the F5 DC Agent service
-
On the Windows-based server, create a user account for F5 DC Agent:
-
Configure the F5 DC Agent service to log on as the user account you just
configured:
Configuring the initialization file
Configuring domain controller polling in the dc_agent.txt file
Recovering from an unsuccessful installation
- Log on to the Windows-based server from a user account with local and domain administrator privilege.
- From the Windows Programs and Features dialog box, uninstall the F5 Installer application.
- From Windows Explorer, click the DC Agent.exe file and follow the instructions to install F5 DC Agent again.
Troubleshooting when a user is identified incorrectly
- Log on to the client system that belongs to the user.
- Open a browser and navigate to four or more distinctive web sites.
- Log on to the Windows-based server where the F5® DC Agent is installed.
- Look for error messages in the Windows Event Viewer.
- Proceed based on any error messages that you discover.
F5 DC Agent error messages
Error messages from the F5® DC Agent display in the Event Viewer on the Windows-based server where DC Agent is installed.
| Error code | Error message | Possible causes |
|---|---|---|
| 3 | Could not configure DC Agent (Code 3) | An attempt was made to install F5 DC Agent using an account that does not have domain and local administrator privileges. As a result, some required files are not installed properly, and F5 DC Agent service cannot run. |
| 5 | ERROR_ACCESS_DENIED | F5 DC Agent service does not have sufficient permissions to perform required
tasks. This error can occur when:
|
| 53 | ERROR_BAD_NETPATH | A network problem prevents F5 DC Agent from contacting a domain controller. This
error can occur when:
|
| 71 | System error while enumerating the domain controllers. domain: (****)ecode: 71 : message: No more connections can be made to this remote computer at this time because there are already as many connections as the computer can accept. | The error results from F5 DC Agent automatic domain discovery process, used to identify new domains and domain controllers. It can also occur when F5 DC Agent tries to connect to a Windows XP-based computer that is broadcasting itself as the master browser for a non-company domain or workgroup. Although the issue might indicate a problem with connectivity to the domain controller, it is more likely that the domain is a workgroup with no domain controllers. This error can be ignored. |
| 997 | Error Code 997 | An attempt was made to install F5 DC Agent using an account that does not have domain and local administrator privileges. As a result, some required files are not installed properly, and F5 DC Agent service cannot run. |
| 1058 | Error Code 1058 | This error is seen on startup. A Local Security Policy on the Windows-based server might have disabled the F5 DC Agent service. |





