Applies To:
Show Versions
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1, 12.1.0
Per-Request Policy Subroutine for Additional Authentication
About per-request policy subroutines
A per-request policy subroutine is a collection of actions. What distinguishes a subroutine from other collections of actions (such as macros), is that a subroutine starts a subsession that, for its duration, controls user access to specified resources. Subroutine properties not only specify resources but also specify subsession timeout values and maximum subsession duration.
About subsessions
A subsession starts when a subroutine runs and continues until reaching the maximum lifetime specified in the subroutine properties, or until the session terminates. A subsession does not count against license limits. A subsession populates subsession variables that are available for the duration of the subsession. Subsession variables and events that occur during a subsession are logged. Multiple subsessions can exist at the same time.
About typical per-request policy subroutine uses
- Request additional authentication from a user after a period of time or before granting access to sensitive resources.
- Revalidate webtop resources using Active Directory credentials.
- Certificate-based authentication (provided by On-Demand Certificate authentication) when going to a specific URI.
- After SharePoint anonymous access, authenticate a user against Active Directory and do a group lookup.
Additional authentication subroutine example
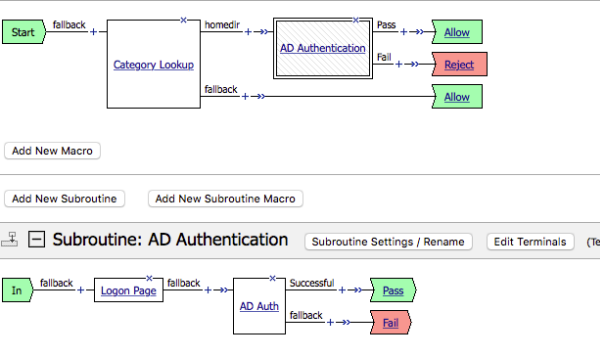
Per-request Policy: Category Lookup and subroutine for authentication
Category Lookup reverse proxy configuration example
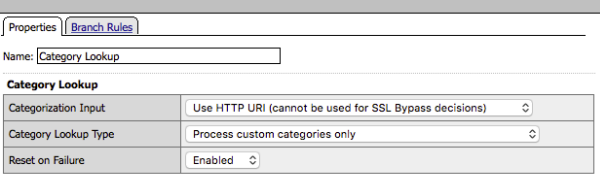
Category Lookup properties for reverse proxy must specify custom categories
Category Lookup branch configuration example
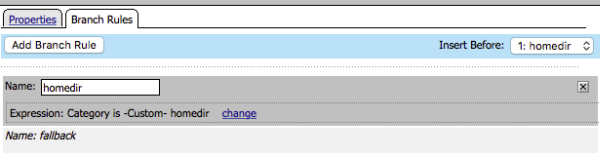
The branch rule specifies the homedir branch and the homedir custom category
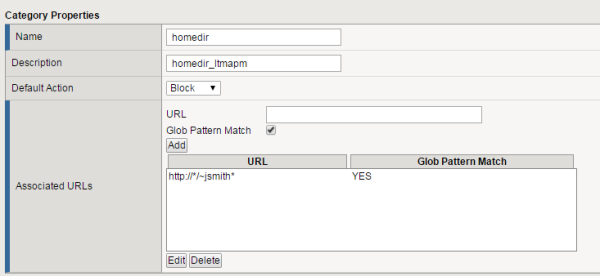
Custom category configuration example
Properties for a custom category homedir
Overview: Requiring additional authentication for sensitive resources
Typically, an access policy verifies endpoint security and authenticates a user before starting an access session. If the user requests access to a sensitive resource after the session is established, you can require additional authentication or revalidation of the credentials for that resource by configuring a per-request policy subroutine.





