Applies To:
Show Versions
BIG-IP AAM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP APM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP Link Controller
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP Analytics
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP LTM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP AFM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP PEM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP DNS
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
BIG-IP ASM
- 13.1.5, 13.1.4, 13.1.3, 13.1.1, 13.1.0, 13.0.1, 13.0.0
Overview: Configuring a custom cipher string for SSL negotiation
Before the BIG-IP® system can process SSL traffic, you need to define the cipher string that you want the system to use when negotiating security settings with client or server systems.
Typing a raw cipher string on the system is tedious and can easily contain typos. It can also be unsecure, since the cipher string could inadvertently cause the system to negotiate in a way that you didn't intend.
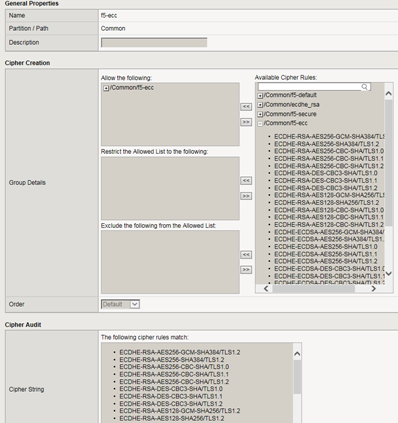
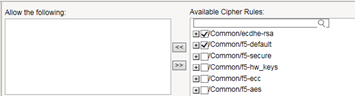
To avoid these problems, you can use cipher rules and cipher groups. With cipher rules and groups, you instruct the BIG-IP system which cipher suites to include and exclude, and the system will build the cipher string for you. This illustration shows the main screen for creating a cipher group.
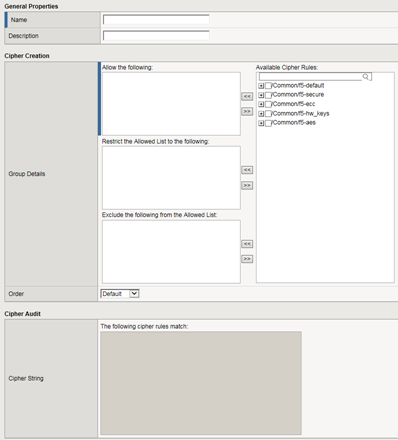
Use of cipher groups and cipher rules is optional.
About BIG-IP cipher support
The BIG-IP® system supports a large set of cipher suites that you can choose from to build the cipher string used for security negotiation.
Supported cipher suites include various combinations of encryption algorithms and authentication mechanisms, including RSA (Rivest Shamir Adleman), DSA (Digital Signature Algorithm), and ECDSA (Elliptic Curve Digital signature Algorithm).
The system includes a default cipher string represented by the keyword DEFAULT, which contains a subset of the cipher suites that the BIG-IP system supports.
What is a cipher rule?
A cipher rule is an object that contains cipher-related information such as an encryption algorithm and a key exchange method. The BIG-IP system will use one or more cipher rules within a cipher group, to build the cipher string that the system will use to negotiate SSL security parameters with a client or server system.
You can use pre-defined cipher rules that the BIG-IP system provides, or you can create your own. In either case, after you decide which cipher rules you want to use, you then specify the cipher rules within a cipher group, which is the object that builds the actual cipher string that the system will use during SSL negotiation. Then you just need to specify the cipher group within a Client SSL or Server SSL profile, and assign the profile to a virtual server.
An example of a cipher rule might be one that specifies only ciphers that use a particular bulk encryption algorithm and a key exchange method.
What is a cipher group?
A cipher group contains a list of cipher rules, and the instructions that the BIG-IP® system needs for building the cipher string it will use for security negotiation. The instructions tell the system which cipher rules to include in the string, and how to apply them (allow, disallow, and so on, and in what order).
Pre-built cipher groups
The BIG-IP system offers a few pre-built cipher groups that you can choose from to use as is to build your final cipher string, However, it's common to create your own custom cipher group instead.
Custom cipher groups
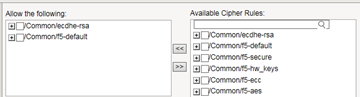
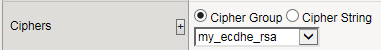
This illustration shows an example of a custom cipher group. Using this cipher group, the BIG-IP system builds the final cipher string using a user-created custom cipher rule named /Common/my_ecdhe_rsa and the pre-built cipher rule /Common/f5-default.
Notice that the system will exclude from the string any cipher suites defined in the pre-built cipher rule /Common/f5-hw_keys.
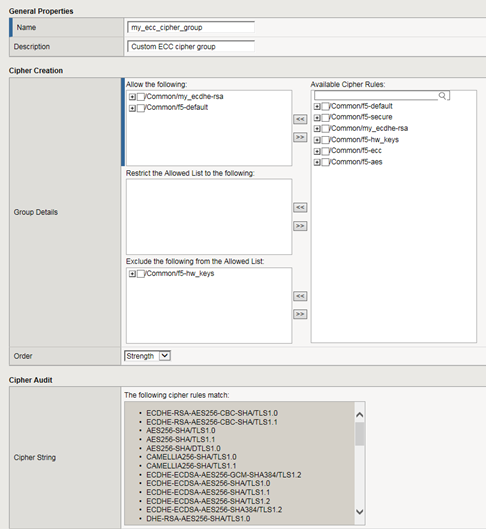
Also notice that the cipher group displays a preview of the final cipher string after the instructions are applied.
Best practices for BIG-IP cipher strings
For security and performance reasons, consider the following recommendations:
- Always append cipher suites to the DEFAULT cipher string.
- Include a cipher string that specifies the ECC key type, because its shorter length speeds up encryption and decryption while still offering virtually the same level of security.
- Disable ADH ciphers but also include the keyword HIGH. To do this, just include both !ADH and :HIGH in your cipher string.
- For AES, DES, and RC4 encryption types, make sure you specify the DHE key exchange method. DHE uses Forward Privacy, which creates a key that it throws away after each session so that the same session key never gets used twice. When you use DHE, make sure that the SSL private key isn't being shared with a monitoring system or a security device like an intrusion detection or prevention system. And by the way, diagnostic tools like ssldump won't work when you're using Forward Secrecy.
- Disable EXPORT ciphers by including !EXPORT in the cipher string.
- If you can live with removing support for the SSLv3 protocol version, do it. This protocol version is unsecure. Simply include :!SSLv3 in any cipher string you build.
View all cipher suites supported by BIG-IP system
Task summary for configuring a custom cipher string
There are a few tasks you need to perform to use cipher rules and cipher groups to configure the cipher string that the BIG-IP® system will use for SSL negotiation.
This illustration shows the order that you need to perform these tasks in.
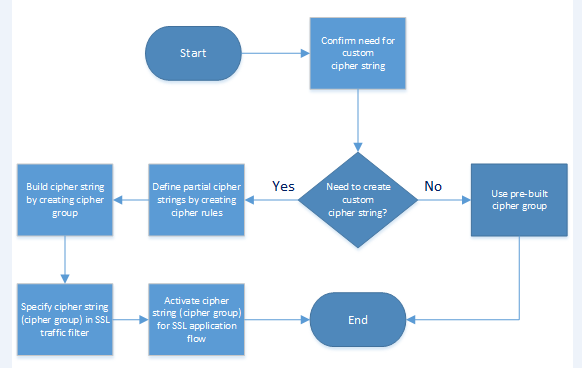
Confirm the need for a custom cipher string
Before you create and deploy a custom cipher string, you can review the pre-built cipher groups on the BIG-IP® system to see if any of them already contains the cipher suites you need.
Create partial cipher strings to include in a custom cipher string
When you create your own cipher rules for a custom cipher group, the BIG-IP® system can build a cipher string that includes or excludes the cipher suites you need for negotiating SSL connections.
Build a custom cipher string
You build a final, custom cipher string by creating a cipher group. A cipher group contains the cipher rules and instructions that the BIG-IP® system needs for building the cipher string it will use for security negotiation with a client or server system.
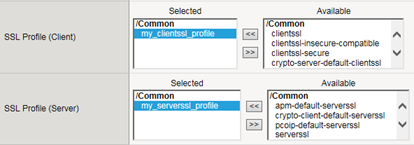
Specify a custom cipher string within an SSL traffic filter
Specifying a custom cipher group within a particular Client SSL or Server SSL profile tells the BIG-IP system which cipher string to use when negotiating security settings.