Applies To:
Show Versions
BIG-IP AAM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP APM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP GTM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP Link Controller
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP LTM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP AFM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP PEM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP ASM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
Using SNAT Auto Map
One of the ways that you can set up all-active clustering of BIG-IP devices is through the use of SNAT Auto Map. This example includes an ECMP-enabled router on the BIG-IP external network and a load balancing pool on the internal network. Each device in the device group has the same virtual IP address and provides a unique, static self IP address for the next-hop route to the virtual server. Furthermore, by enabling SNAT Auto Map on the virtual server, each server response returns through the originating device by way of the unique self IP address on its way back to the client.
This illustration shows an example of this configuration.
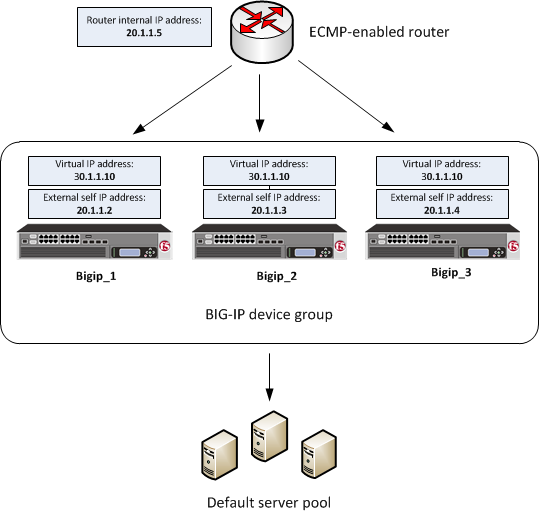 BIG-IP system clustering using ECMP with SNAT Auto Map
BIG-IP system clustering using ECMP with SNAT Auto Map
Creating a load balancing pool
Creating a virtual server
Confirming virtual address exclusion from a traffic group
Syncing the BIG-IP configuration to the device group
Configuring the BGP protocol
Perform this task when you want to configure the Border Gateway Protocol (BGP) dynamic routing protocol.
Sample BGP configuration using SNAT Auto Map
This example shows part of an example of Border Gateway Protocol (BGP) configuration on a BIG-IP device that accepts traffic from an upstream ECMP-enabled router.
| Configuration entry | Description |
|---|---|
| bgp router-id 20.1.1.2 | The bgp router-id value is the self IP address for the external VLAN on device Bigip_1. This address must be unique within the BGP configuration on each BIG-IP device in the device group. |
| neighbor 20.1.1.5 | The neighbor value is the IP address of the ECMP-enabled router. You must repeat the neighbor statement for each upstream router associated with a BIG-IP device. These neighbor statements are the same within the BGP configuration on each BIG-IP device in the device group. |
| ip prefix-list | The ip prefix-list entry specifies that the virtual IP address 30.1.1.10/32 is allowed to be advertised. |
| set ip next-hop 20.1.1.2 | The set ip next-hop value is the self IP address for the external VLAN on device Bigip_1. This next-hop address is used for traffic that is destined for the virtual IP address and potentially the specified SNAT pool address. This address must be unique within the BGP configuration on each BIG-IP device in the device group. |
Implementation result
After following the instructions in this implementation, you now have a three-member BIG-IP device group, where the same virtual server resides on each device, and each device is configured for dynamic routing using the Border Gateway Protocol (BGP). Also, the external self IP address that you created on each device is configured to allow the upstream ECMP-enabled router to send traffic through port 179 on each BIG-IP device.
With this configuration, when application traffic comes through the ECMP-enabled router, the router can use an algorithm to choose the best equal-cost path to any one of the BIG-IP devices in the device group. If any BIG-IP device becomes unavailable, the ECMP algorithm causes the ECMP-enabled router to forward that traffic to another device in the device group. Furthermore, each BIG-IP device has an administrative partition whose local traffic objects are synchronized to the devices in the Sync-Only device group. All devices in the device group use the default load balancing pool to process application traffic.





