Applies To:
Show Versions
BIG-IP AAM
- 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP Analytics
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP Link Controller
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP LTM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP AFM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP PEM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP DNS
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
BIG-IP ASM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2
Configuring Remote High-Speed DNS Logging
Overview: Configuring remote high-speed DNS logging
You can configure the BIG-IP® system to log information about DNS traffic and send the log messages to remote high-speed log servers. You can choose to log either DNS queries or DNS responses, or both. In addition, you can configure the system to perform logging on DNS traffic differently for specific resources. For example, you can configure logging for a specific resource, and then disable and re-enable logging for the resource based on your network administration needs.
This illustration shows the association of the configuration objects for remote high-speed logging.
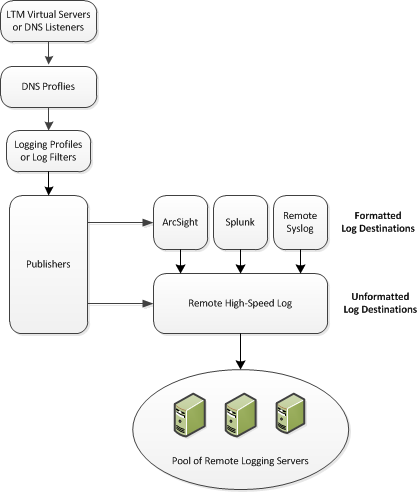
Association of remote high-speed logging configuration objects
Task summary
About the configuration objects of remote high-speed DNS logging
When configuring remote high-speed DNS logging, it is helpful to understand the objects you need to create and why, as described here:
| Object | Reason | Applies to |
|---|---|---|
| Pool of remote log servers | Create a pool of remote log servers to which the BIG-IP® system can send log messages. | Creating a pool of remote logging servers. |
| Destination (unformatted) | Create a log destination of Remote High-Speed Log type that specifies a pool of remote log servers. | Creating a remote high-speed log destination. |
| Destination (formatted) | If your remote log servers are the ArcSight, Splunk, IPFIX, or Remote Syslog type, create an additional log destination to format the logs in the required format and forward the logs to a remote high-speed log destination. | Creating a formatted remote high-speed log destination. |
| Publisher | Create a log publisher to send logs to a set of specified log destinations. | Creating a publisher. |
| DNS Logging profile | Create a custom DNS Logging profile to define the data you want the BIG-IP system to include in the DNS logs and associate a log publisher with the profile. | Creating a custom DNS logging profile for logging DNS queries. Creating a custom DNS logging profile for logging DNS responses. Creating a custom DNS logging profile for logging DNS queries and responses. |
| DNS profile | Create a custom DNS profile to enable DNS logging, and associate a DNS Logging profile with the DNS profile. | Creating a custom DNS profile to enable DNS logging. |
| LTM® virtual server | Associate a custom DNS profile with a virtual server to define how the BIG-IP system logs the DNS traffic that the virtual server processes. | Configuring an LTM virtual server for DNS logging. |
Creating a pool of remote logging servers
Creating a remote high-speed log destination
Create a log destination of the Remote High-Speed Log type to specify that log messages are sent to a pool of remote log servers.
Creating a formatted remote high-speed log destination
Create a formatted logging destination to specify that log messages are sent to a pool of remote log servers, such as Remote Syslog, Splunk, or ArcSight servers.
Creating a publisher
Creating a custom DNS logging profile for logging DNS queries
Creating a custom DNS logging profile for logging DNS responses
Creating a custom DNS logging profile for logging DNS queries and responses
Creating a custom DNS profile to enable DNS logging
Configuring a listener for DNS logging
Configuring an LTM virtual server for DNS logging
Configuring logs for global server load-balancing decisions
Disabling DNS logging
Implementation result
You now have an implementation in which the BIG-IP® system performs DNS logging on specific DNS traffic and sends the log messages to a pool of remote log servers.





