Applies To:
Show Versions
BIG-IP ASM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1, 12.1.0
Using Vulnerability Assessment Tools for a Security Policy
Overview: Vulnerability assessment policy building
- HP WebInspect
- IBM®AppScan®
- Qualys®
- Quotium Seeker®
- Trustwave ® App Scanner
- WhiteHat Sentinel
You can use the vulnerability assessment deployment scenario to create a baseline security policy that is integrated with a vulnerability assessment tool. By using vulnerability assessment tool output, the system suggests updates to the security policy that can protect against the vulnerabilities that the tool found. You can choose which of the vulnerabilities you want the security policy to handle, retest to be sure that the security policy protects against the vulnerabilities, then enforce the security policy when you are ready.
If you have an existing security policy that was created using a different deployment scenario, you can also incorporate use of a vulnerability assessment tool with that policy.
Task summary
About using Policy Builder with scanner policies
When you develop a security policy using third party vulnerability assessment tool or scanner output, you can set the Learning Mode to automatic or manual, which enables the Real Traffic Policy Builder®. In this case, the Policy Builder makes suggestions for what to add to the policy based on what it learns from your web application traffic, and uses logic to prevent false positives. The suggestions are either automatically learned by the system or they must be manually learned by an administrator depending on the learning mode you selected.
In addition, you select an external scanning tool such as WhiteHat Sentinel, Qualys Web Application Scanning, IBM AppScan, Trustwave App Scanner (Cenzic), Quotium Seeker, or others to build your policy to protect against the vulnerabilities they have found. You import the vulnerabilities detected by the scanner, and choose whether or not to update the security policy for each problem found.
It is possible that in some cases Policy Builder decisions might conflict with and override the scanner results. Here are some examples:
- The Policy Builder might remove a URL that the scanner added to the list of CSRF-protected URLs.
- The Policy Builder might allow file upload of executable files on a parameter after the scanner disallowed it.
- The Policy Builder might add an allowed method after the scanner disallowed it.
- The Policy Builder might disable attack signatures on parameters, cookies, and at the policy level after the scanner enabled them.
You can also select disabled for the Learning Mode, which disables the Policy Builder so that it does not make learning suggestions. In this case, you can manually build the security policy or just use scanner output to build it. You can adjust the Learning Mode after creating the policy on the Policy Building Learning and Blocking Settings screen.
About exporting results from scanners
Application Security Manager™ (ASM) integrates with the current version of many vulnerability assessment tools (also called scanners). ASM uses the exported results from the scanners to address potential vulnerabilities or security risks concerning your application web site. Using a scanner external to ASM, you perform a vulnerability assessment of the web site, then export the results in standard XML format. Then later, using ASM, you import the results into the security policy being developed to protect the application.
Here are brief instructions on how to export the scan results from several of the vulnerability assessment tools.
| Tool | To export scan results from the tool |
|---|---|
| Trustwave App Scanner | Right click . |
| HP WebInspect | Click . Export the Full details in XML format. |
| IBM AppScan | Click . |
| Qualys | Click . |
| Quotium Seeker | Click , select F5 BIG-IP ASM format. In ASM, use Generic Scanner to configure. |
| WhiteHat Sentinel | Retrieves reports by connecting directly to ASM using a web service. |
You can use additional vulnerability assessment tools as long as you have the results in standard XML output.
Creating a security policy using vulnerability assessment tool output
Before you can create a security policy using ASM™, you need to complete the basic BIG-IP® system configuration tasks including creating a VLAN, a self IP address, and other tasks, according to the needs of your networking environment.
Associating a vulnerability assessment tool with an existing security policy
Importing vulnerability assessment tool output
Resolving vulnerabilities
Reviewing learning suggestions
After you create a security policy, the system provides learning suggestions concerning additions to the security policy based on the traffic that is accessing the application. For example, you can have users or testers browse the web application. By analyzing the traffic to and from the application, Application Security Manager™ generates learning suggestions or ways to fine-tune the security policy to better suit the traffic and secure the application.
Learning suggestions you must handle manually
Some learning suggestions must be resolved manually even if you are using the Automatic Learning Mode to create a security policy. Suggestions typically require manual intervention if they involve changing an attribute that was manually and deliberately set in the policy, such as a disallowed geolocation or a session ID in a URL. The system does not change the policy unless you accept the suggestion manually.
You can easily see the suggestions that you need to resolve manually because they are marked with an icon on the Traffic Learning screen as shown in the figure. You can also use the advanced filter to view the suggestions the have Learning Mode set to Manual, and this would list the suggestions you need to resolve.
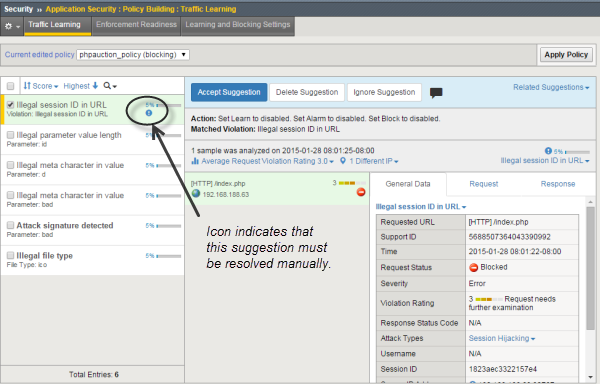
Suggestions that must be resolved manually
If you are using the Manual Learning Mode, you must resolve all of the suggestions manually.





