Applies To:
Show Versions
BIG-IP APM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
Overview: Configuring transparent forward proxy in inline mode
In transparent forward proxy, you configure your internal network to forward web traffic to the BIG-IP system with Secure Web Gateway (SWG). This implementation describes an inline deployment. You place the BIG-IP system directly in the path of traffic, or inline, as the next hop after the gateway.
 Secure Web Gateway transparent forward proxy inline deployment
Secure Web Gateway transparent forward proxy inline deployment
The gateway sends traffic to the self-ip address of a VLAN configured on the BIG-IP system. Wildcard virtual servers listen on the VLAN and process the traffic that most closely matches the virtual server address. A wildcard virtual server is a special type of network virtual server designed to manage network traffic that is targeted to transparent network devices. SWG identifies users without using session management cookies, and applies a scheme that categorizes and filters URLs, controlling access.
Task Summary
SWG transparent forward proxy configuration prerequisites
To use Secure Web Gateway (SWG), you must configure URL categorization. You might need to configure additional items depending on the other features that you decide to use.
- URL categorization
- To get a working SWG configuration, you must first download URL categories, configure URL filters, and configure schemes.
- Transparent user identification
- If you plan to identify users transparently, you must first download, install, and configure a BIG-IP user identification agent, either the F5 DC Agent or the F5 Logon Agent.
- Authentication
- F5 recommends that you use NTLM or Kerberos authentication. If you plan to use
authentication, ensure that you have what you need configured.
- For NTLM, you need an NTLM Auth Configuration in Access Policy Manager (APM).
- For Kerberos, you need a domain-joined Kerberos user account and a Kerberos AAA server configured in APM.
- SSL intercept
- To intercept SSL connections that are passing through the proxy, ensure that you have imported a valid subordinate CA certificate and key that is trusted by the endpoints behind the proxy.
- Captive portal
- If you plan to use the captive portal feature, make sure that a certificate and key with the proper common name is imported for use.
About the iApp for Secure Web Gateway configuration
When deployed as an application service, the Secure Web Gateway iApps template can set up either an explicit or a transparent forward proxy configuration. You can download the template from the F5 DevCentral iApp Codeshare wiki at (http://devcentral.f5.com/wiki/iapp.Codeshare.ashx).
About ways to configure user identification for SWG
User identification configuration requires a method setting in the access profile and an access policy configured to support the setting. Depending on the access profile type, you can select one of these user identification methods: by IP address (for SWG-Explicit or SWG-Transparent access profile types) or by credentials (for SWG-Explicit type).
Identification by IP address
When you identify users by IP address, you can employ any of these methods.
- transparent user identification
- Transparent user identification makes a best effort to identify users without
requesting credentials.
An agent obtains
data and stores a mapping of IP addresses to user names in an IF-MAP server. An F5 DC
Agent queries domain controllers. An F5 Logon Agent runs a script when a client logs in
and can run a script when the client logs out. Note: To identify users transparently, you must first install and configure one BIG-IP user identification agent, either the F5 DC Agent or the F5 Logon Agent.
- explicit user identification
- You can present a logon page in an access policy to request user credentials and validate them. SWG maintains an internal mapping of IP addresses to user names. (You can present the appropriate logon page for the access policy type. For explicit forward proxy, you can present a 407 page. For transparent forward proxy, you can present a 401 page.)
- source IP ranges or subnets
- You can forego actually identifying the user and base the choice of which scheme to apply on whether the IP address is in a source IP range or on a subnet. SWG maintains an internal mapping of IP addresses to sessions.
Identification by credentials
When you choose to identify users by credentials, SWG maintains an internal mapping of credentials to sessions. To support this choice, you need an NTLM Auth Configuration object and you should check the result of NTLM authentication in the access policy.
Creating a VLAN for transparent forward proxy
Assigning a self IP address to a VLAN
Configuring a per-request policy for SWG
Creating an access profile for SWG transparent forward proxy
Configuring an access policy for transparent forward proxy
Creating a custom Client SSL forward proxy profile
Creating a Client SSL forward proxy profile makes it possible for client and server authentication, while still allowing the BIG-IP system to perform data optimization, such as decryption and encryption. This profile applies to client-side SSL forward proxy traffic only.
Creating a custom Server SSL profile
Creating a virtual server for forward proxy SSL traffic
Creating a virtual server for forward proxy traffic
Creating a forwarding virtual server
Creating a Client SSL profile for a captive portal
You create a Client SSL profile when you want the BIG-IP system to authenticate and decrypt/encrypt client-side application traffic. You create this profile if you enabled Captive Portals in the access profile and if you want to use SSL.
Creating a virtual server for a captive portal
Implementation result
Web traffic that originates from your enterprise networks is now inspected and controlled by F5 Secure Web Gateway forward proxy.
Session variables for use in a per-request policy
Per-request policy items that look up the group or class to which a user belongs rely on the access policy to populate these session variables.
| Per-request policy item | Session variable | Access policy item |
|---|---|---|
| AD Group Lookup | session.ad.last.attr.primaryGroupID | AD Query |
| LDAP Group Lookup | session.ldap.last.attr.memberOf | LDAP Query |
| LocalDB Group Lookup | session.localdb.groups
Note: This session variable is a default in the expression for LocalDB
Group Lookup; any session variable in the expression must match the session variable
used in the Local Database action in the access policy.
|
Local Database |
| RADIUS Class Lookup | session.radius.last.attr.class | RADIUS Auth |
About redirects after access denied by captive portal
A tool that captures HTTP traffic can reveal what appears to be an extra redirect after a user attempts to gain access using a captive portal but fails, and the access policy goes to a Deny ending. Instead of immediately redirecting the user to the logout page, the user is first redirected to the landing URI, and then a request to the landing URI is redirected to the logout page.
This sample output shows both redirects: the 302 to the landing page http://berkeley.edu/index.html and the 302 to the logout page http://berkeley.edu/vdesk/hangup.php3.
POST https://bigip-master.com/my.policy?ORIG_URI=http://berkeley.edu/index.html 302 http://berkeley.edu/index.html GET http://berkeley.edu/index.html 302 http://berkeley.edu/vdesk/hangup.php3Although the 302 to the landing page might seem to be an extra redirect, it is not. When a request is made, a subordinate virtual server transfers the request to the dominant virtual server to complete the access policy. When the dominant virtual completes the access policy, it transfers the user back to the subordinate virtual server, on the same original request. The subordinate virtual server then enforces the result of the access policy.
Overview: Configuring transparent forward proxy
In transparent forward proxy, you configure your internal network to forward web traffic to the BIG-IP system with Secure Web Gateway (SWG). Use this implementation when your topology includes a router on which you can configure policy-based routing or Web Cache Communication Protocol (WCCP) to send any traffic for ports 80 and 443 to the BIG-IP system.
This implementation describes only the configuration required on the BIG-IP system.
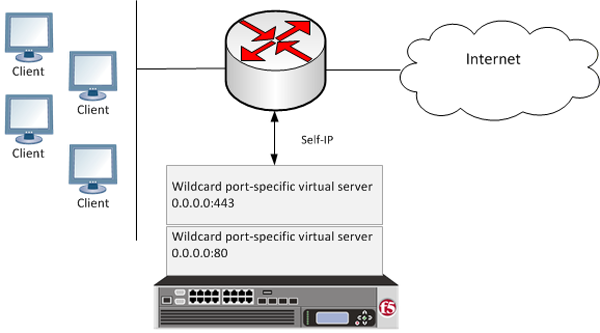 Secure Web Gateway transparent forward proxy deployment
Secure Web Gateway transparent forward proxy deployment
The router sends traffic to the self-ip address of a VLAN configured on the BIG-IP system. Virtual servers listen on the VLAN and process the traffic that most closely matches the virtual server address. Secure Web Gateway identifies users without using session management cookies, and applies a scheme that categorizes and filters URLs, controlling access.
Task Summary
SWG transparent forward proxy configuration prerequisites
To use Secure Web Gateway (SWG), you must configure URL categorization. You might need to configure additional items depending on the other features that you decide to use.
- URL categorization
- To get a working SWG configuration, you must first download URL categories, configure URL filters, and configure schemes.
- Transparent user identification
- If you plan to identify users transparently, you must first download, install, and configure a BIG-IP user identification agent, either the F5 DC Agent or the F5 Logon Agent.
- Authentication
- F5 recommends that you use NTLM or Kerberos authentication. If you plan to use
authentication, ensure that you have what you need configured.
- For NTLM, you need an NTLM Auth Configuration in Access Policy Manager (APM).
- For Kerberos, you need a domain-joined Kerberos user account and a Kerberos AAA server configured in APM.
- SSL intercept
- To intercept SSL connections that are passing through the proxy, ensure that you have imported a valid subordinate CA certificate and key that is trusted by the endpoints behind the proxy.
- Captive portal
- If you plan to use the captive portal feature, make sure that a certificate and key with the proper common name is imported for use.
About the iApp for Secure Web Gateway configuration
When deployed as an application service, the Secure Web Gateway iApps template can set up either an explicit or a transparent forward proxy configuration. You can download the template from the F5 DevCentral iApp Codeshare wiki at (http://devcentral.f5.com/wiki/iapp.Codeshare.ashx).
About ways to configure user identification for SWG
User identification configuration requires a method setting in the access profile and an access policy configured to support the setting. Depending on the access profile type, you can select one of these user identification methods: by IP address (for SWG-Explicit or SWG-Transparent access profile types) or by credentials (for SWG-Explicit type).
Identification by IP address
When you identify users by IP address, you can employ any of these methods.
- transparent user identification
- Transparent user identification makes a best effort to identify users without
requesting credentials.
An agent obtains
data and stores a mapping of IP addresses to user names in an IF-MAP server. An F5 DC
Agent queries domain controllers. An F5 Logon Agent runs a script when a client logs in
and can run a script when the client logs out. Note: To identify users transparently, you must first install and configure one BIG-IP user identification agent, either the F5 DC Agent or the F5 Logon Agent.
- explicit user identification
- You can present a logon page in an access policy to request user credentials and validate them. SWG maintains an internal mapping of IP addresses to user names. (You can present the appropriate logon page for the access policy type. For explicit forward proxy, you can present a 407 page. For transparent forward proxy, you can present a 401 page.)
- source IP ranges or subnets
- You can forego actually identifying the user and base the choice of which scheme to apply on whether the IP address is in a source IP range or on a subnet. SWG maintains an internal mapping of IP addresses to sessions.
Identification by credentials
When you choose to identify users by credentials, SWG maintains an internal mapping of credentials to sessions. To support this choice, you need an NTLM Auth Configuration object and you should check the result of NTLM authentication in the access policy.
Creating a VLAN for transparent forward proxy
Assigning a self IP address to a VLAN
Configuring a per-request policy for SWG
Creating an access profile for SWG transparent forward proxy
Configuring an access policy for transparent forward proxy
Creating a custom Client SSL forward proxy profile
Creating a Client SSL forward proxy profile makes it possible for client and server authentication, while still allowing the BIG-IP system to perform data optimization, such as decryption and encryption. This profile applies to client-side SSL forward proxy traffic only.
Creating a custom Server SSL profile
Creating a virtual server for forward proxy SSL traffic
Creating a virtual server for forward proxy traffic
Creating a Client SSL profile for a captive portal
You create a Client SSL profile when you want the BIG-IP system to authenticate and decrypt/encrypt client-side application traffic. You create this profile if you enabled Captive Portals in the access profile and if you want to use SSL.
Creating a virtual server for a captive portal
Implementation result
Web traffic that originates from your enterprise networks is now inspected and controlled by F5 Secure Web Gateway forward proxy.
Session variables for use in a per-request policy
Per-request policy items that look up the group or class to which a user belongs rely on the access policy to populate these session variables.
| Per-request policy item | Session variable | Access policy item |
|---|---|---|
| AD Group Lookup | session.ad.last.attr.primaryGroupID | AD Query |
| LDAP Group Lookup | session.ldap.last.attr.memberOf | LDAP Query |
| LocalDB Group Lookup | session.localdb.groups
Note: This session variable is a default in the expression for LocalDB
Group Lookup; any session variable in the expression must match the session variable
used in the Local Database action in the access policy.
|
Local Database |
| RADIUS Class Lookup | session.radius.last.attr.class | RADIUS Auth |
About redirects after access denied by captive portal
A tool that captures HTTP traffic can reveal what appears to be an extra redirect after a user attempts to gain access using a captive portal but fails, and the access policy goes to a Deny ending. Instead of immediately redirecting the user to the logout page, the user is first redirected to the landing URI, and then a request to the landing URI is redirected to the logout page.
This sample output shows both redirects: the 302 to the landing page http://berkeley.edu/index.html and the 302 to the logout page http://berkeley.edu/vdesk/hangup.php3.
POST https://bigip-master.com/my.policy?ORIG_URI=http://berkeley.edu/index.html 302 http://berkeley.edu/index.html GET http://berkeley.edu/index.html 302 http://berkeley.edu/vdesk/hangup.php3Although the 302 to the landing page might seem to be an extra redirect, it is not. When a request is made, a subordinate virtual server transfers the request to the dominant virtual server to complete the access policy. When the dominant virtual completes the access policy, it transfers the user back to the subordinate virtual server, on the same original request. The subordinate virtual server then enforces the result of the access policy.





