Applies To:
Show Versions
BIG-IP APM
- 12.1.6, 12.1.5, 12.1.4, 12.1.3, 12.1.2, 12.1.1, 12.1.0
Integrating Portal Access and Secure Web Gateway
Overview: Configuring SWG transparent forward proxy for remote access
Secure Web Gateway (SWG) can be configured to support remote clients that connect using application access, network access, or portal access.
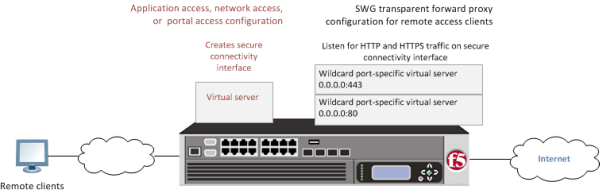
SWG transparent forward proxy for remote access
Task summary
Prerequisites for SWG transparent forward proxy for remote access
Before you start to create a Secure Web Gateway (SWG) transparent forward proxy configuration to support remote access clients, you must have completed these tasks.
- You must have a working Network Access, Portal Access, or Application Access configuration.
- You need a per-request policy configured for forward proxy.
- On a BIG-IP® system with an SWG subscription, you must ensure that the URL database is downloaded and you need to have configured any URL filters that you want to use in addition to, or instead of, the default URL filters.
- On a BIG-IP® system without an SWG subscription to use URL categories and filters, you must have created user-defined URL categories and URL filters.
Configuration outline for SWG transparent forward proxy for remote access
Tasks for integrating an Access Policy Manager® (APM®) remote access configuration with a Secure Web Gateway (SWG) transparent forward proxy configuration follow this order.
- First, update the existing application access, network access, or portal access configuration to add a secure connectivity profile to the virtual server if one is not already specified.
- Next, create an SWG transparent forward proxy configuration. The per-request policy is part of this configuration.
- Finally, update the access policy in the existing application access, network access, or portal access configuration if needed. If the per-request policy uses group or class lookup items, add queries to the access policy to populate the session variables on which the lookup items rely.
Creating a connectivity profile
Adding a connectivity profile to a virtual server
Update a virtual server that is part of an Access Policy Manager® application access, network access, or portal access configuration to enable a secure connectivity interface for traffic from the client.
Creating an access profile for SWG transparent forward proxy
Verifying log settings for the access profile
Creating a wildcard virtual server for HTTP traffic on the connectivity interface
Creating a custom Client SSL forward proxy profile
Creating a Client SSL forward proxy profile makes it possible for client and server authentication, while still allowing the BIG-IP® system to perform data optimization, such as decryption and encryption. This profile applies to client-side SSL forward proxy traffic only.
Creating a custom Server SSL profile
Creating a wildcard virtual server for SSL traffic on the connectivity interface
Updating the access policy in the remote access configuration
Add queries to the access policy to populate any session variables that are required for successful execution of the per-request policy.
Implementation result
The Secure Web Gateway (SWG) transparent proxy configuration is ready to process web traffic from remote access clients.
About configuration elements for transparent forward proxy (remote access)
When you configure Secure Web Gateway (SWG) transparent forward proxy for use by remote access clients, you might want to understand how these objects fit into the overall configuration.
- Secure connectivity interface
- In a remote access configuration, a connectivity profile is required on the virtual server to specify a secure connectivity interface for traffic from the client. In the SWG configuration, SWG wildcard virtual servers must listen on the secure connectivity interface for traffic from remote access clients.
- Per-request policy
- In any SWG configuration, the determination of whether a user can access a URL must be made in a per-request access policy. A per-request access policy determines whether to block or allow access to a request based on time or date or group membership or other criteria that you configure.
- Access policies
- The access policy in the remote access configuration continues to authenticate users, assign resources, and evaluate ACLs, if any. In addition, this access policy must populate any session variables used in the per-request policy. An access profile of the SWG-Transparent type is required in the SWG configuration; however, it is not necessary to include any items in the access policy.
Per-request policy items that read session variables
This table lists per-request policy items that read session variables and lists the access policy items that populate the variables.
| Per-request policy item | Session variable | Access policy item |
|---|---|---|
| AD Group Lookup | session.ad.last.attr.primaryGroupID | AD Query |
| LDAP Group Lookup | session.ldap.last.attr.memberOf | LDAP Query |
| LocalDB Group Lookup |
session.localdb.groups
Note: This session variable is a default in the expression for LocalDB
Group Lookup; any session variable in the expression must match the session variable
used in the Local Database action in the access policy.
|
Local Database |
| RADIUS Class Lookup | session.radius.last.attr.class | RADIUS Auth |





