Before you start this task, configure an access profile and configure a form action that uses an external SMS to send the one-time password.
Create an access policy like this when you need to generate and send a one-time password as a text message and you do not want to send it using email.
Note: The macro, AD auth query OTP by HTTP and resources, is available from the visual policy editor and might be useful to configure an access policy similar to this one.
- On the Main tab, click . The Access Profiles List screen opens.
- In the Access Policy column, click the Edit link for the access profile you want to configure. The visual policy editor opens the access policy in a separate screen.
- Add actions to authenticate the user and find a mobile phone number.
- Click the (+) icon anywhere in your access profile to add a new action item. An popup screen opens, listing predefined actions on tabs such as General Purpose, Authentication, and so on.
- From the Authentication tab, select AD Auth and click Add Item. A pop-up properties screen displays.
- From the Server list, select a server and click Save. The properties screen closes.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- On the Authentication tab, select AD Query and click Add Item. A pop-up properties screen displays.
- From the Server list, select a server.
- Click Add new entry. An empty entry displays under Required Attributes (optional).
- Type mobile into the Required Attributes (optional) field
- Click Save. The properties screen closes.
- Generate a one-time password.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- From the Authentication tab, select OTP Generate and click Add Item.
- Click Save. The properties screen closes and the visual policy editor is displayed.
- Make the OTP secure.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- From the Assignment tab, select Variable Assign and click Add Item. A properties screen opens.
- Click Add new entry. An Empty entry displays.
- Click the change link in the new entry. A popup screen opens.
- From the Unsecure list, select Secure.
- In the Custom Variable text box, type session.user.otp.pwd.
- In the Custom Expression text box, type expr { [mcget {session.user.otp.pw}]}.
- Click Finished. The popup screen closes.
- Send the OTP through the HTTP Auth agent.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- From the Authentication tab, select HTTP Auth and click Add Item.
- From the AAA server list, select the HTTP form-based server that you configured previously.
- Click Save. The properties screen closes and the visual policy editor is displayed.
- Add a Logon Page action that requests only the one-time password.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- From the Logon Page tab, select Logon Page and click Add Item. A pop-up properties screen displays.
- From the Logon Page Agent area, on line 1 select password from the Type column and change the post and session variable names. The variable name password is acceptable.
- From the Customization area in Logon Page Input Field # 1, type a prompt for the field. For example, type One-Time Passcode.
- Click Save. The properties screen closes and the visual policy editor is displayed.
- Verify the one-time password.
- On the Successful branch after the previous action, click the (+) icon. An Add Item screen opens, listing predefined actions that are grouped on tabs such as General Purpose, Authentication, and so on.
- From the Authentication tab, select OTP Verify and click Add Item.
- Click Save. The properties screen closes and the visual policy editor is displayed.
- Optional: Add any other branches and actions that you need to complete the access policy.
- Change the Successful rule branch from Deny to Allow and click the Save button.
- At the top of the window, click the Apply Access Policy link to apply and activate your changes to this access policy.
- Click the Close button to close the visual policy editor.
You have an access policy that uses HTTP authentication to provide a user with a one-time time-based password over SMS.
To put the access policy into effect, you must attach it to a virtual server.

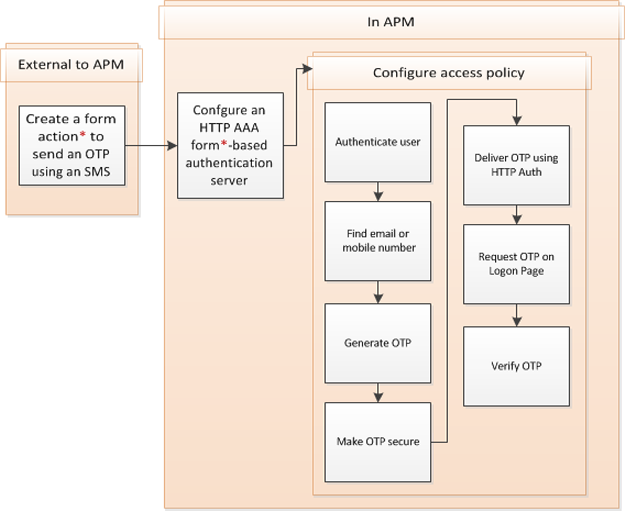 Creating a configuration to send an OTP over SMS using HTTP authentication
Creating a configuration to send an OTP over SMS using HTTP authentication




